Como cada trimestre, analizamos las las notas de seguridad publicadas por SAP, en este caso, analizaremos las del primer trimestre de 2018.
No tenemos notas críticas (Hot News) en este trimestre, por lo tanto, centraremos la revisión en detalle en las 11 notas de nivel alto.
- Destacar que las dos notas de valoración más alta del trimestre (CVSS de 8.8 y de 8.3 respectivamente) están relacionadas con el componente: SAP Internet Graphics Server (IGS).
- La tercera nota, que iguala en valoración a la segunda (es decir CVSS de 8.3.) es del tipo “Missing Authorization Check” en el componente: “SAP NetWeaver System Landscape Directory”.
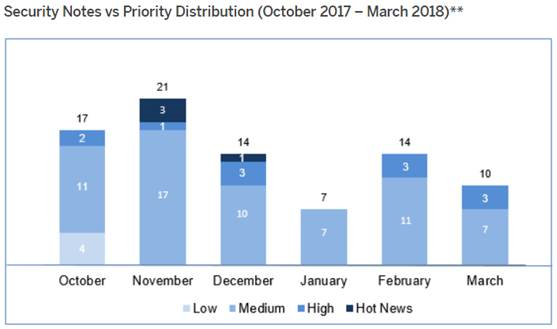
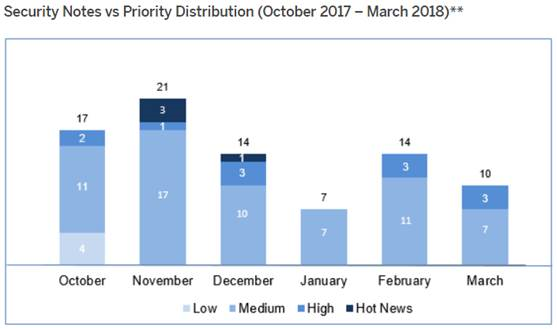
Tenemos un total de 63 notas para todo el trimestre (31 de los patch tuesday):
- En Enero se han publicado un total de 10 notas (7 en el Security Notes Tuesday – 3 nuevas y 4 actualizaciones de notas anteriores).
- En este mes no existen ni “hot news” (críticas) ni notas de criticidad alta (high priority), en efecto en el Patch Day solo tenemos notas de nivel medio (7) a las que se le añaden 2 medias y 2 bajas en el mes completo.
- Nos centraremos en 4 notas de nivel medio, aquellas con un valor de CVSS mayor que 6, que en realidad se reducen a 2, ya que 3 de ellas (“1906212”, “2278931” y “2525392”) están relacionadas con un problema de Inyección de Código (“Code injection vulnerability in Knowledge Provider”) y relacionadas entre sí con el mismo CVSS de 6.5. Por último, destacar una nota de Solution Manager en relación a un error de diseño en un role (autorizaciones) con CVSS de 6.3.
- Este mes el tipo más predominante es de “Missing Authorization Check” (4/10 y 1/7 en patch day), seguido de inyección de código – “Code Injection” (3/10 y 3/7 en patch day).
- En Febrero se han publicado un total de 26 notas (14 en el Security Notes Tuesday – 11 nuevas y 3 actualizaciones de notas anteriores).
- En este mes no existe “hot news” (críticas), pero hay un total de 5 de criticidad alta (high priority), 3 del Patch Day, estando la más importante relacionada con el componente: SAP Internet Graphics Server (IGS) de CVSS 8.3.
- A destacar que SAP está usando la estrategia de sacar notas donde agrupa la corrección de varias vulnerabilidades (en “bundle”) y esto queda patente en 2 casos concretos de este mes, teniendo una nota con referencia a 8 vulnerabilidades corregidas (2525222) y otra con 13 vulnerabilidades corregidas de referencia que es la mencionada antes para el componente IGS (2525222).
- De nuevo, el tipo más predominante es de “Missing Authorization Check” (7/26 y 2/14 en patch day), seguido de “Cross-Site-Scripting – XSS” (5/26 y 3/14 en patch day).
- En Marzo se han publicado un total de 27 notas (10 en el Security Notes Tuesday – 8 nuevas y 2 actualizaciones de notas anteriores).
- En este mes no existe “hot news” (críticas), pero hay un total de 6 de criticidad alta (high priority), 3 del Patch Day, siendo una de estas últimas la nota más relevante del trimestre con un CVSS de 8.8.
- A destacar que la nota más importante, al igual que en Febrero está relacionada con el componente: SAP Internet Graphics Server (IGS) y en este caso con 3 vulnerabilidades distintas relacionadas (3 CVEs).
- Y de nuevo este mes, el tipo más predominante es de “Missing Authorization Check” (6/27 y 1/10 en patch day), seguido muy de cerca de “Information Disclosure” (5/27 y 4/10 en patch day).
En la gráfica (post Marzo 2018 de SAP) podemos ver la evolución y clasificación de las notas de los 3 meses del primer trimestre del año (2018), además de los 3 meses del pasado trimestre (solo las notas del Sec. Tuesday / Patch Day – by SAP):
El detalle completo de las notas más relevantes es el siguiente (en inglés):
- SAP Knowledge Provider has an ABAP code injection vulnerability (2525392): Depending on the code, attackers can inject and run their own code, obtain additional information that should not be displayed, change and delete data, modify the output of the system, create new users with higher privileges, control the behavior of the system, or escalate privileges by executing malicious code or even perform a DOS attack. Install this SAP Security Note to prevent the risks. This note is related to other 2 already mentioned (“1906212”, “2278931”). CVSS v3 Base Score: 6.5 / 10
- SAP Solution Manager 7.2 has an Improper Role Authorizations vulnerability (2507934): Perpetrators can use Improper Role authorizations redundant right to edit all tables on the server. This can lead to compromising data. Install this SAP Security Note to prevent the risks. CVSS v3 Base Score: 6.3 / 10
- SAP Internet Graphics Server (IGS) has an Security vulnerabilities (2525222): Depending on the vulnerability (from the 13 CVE vulnerabilities in reference), attackers can use Denial of service vulnerability for terminating a process of vulnerable component. For this time nobody can use this service, this fact negatively influences on a business processes, system downtime and business reputation as result or use XML external entity vulnerability to send specially crafted unauthorized XML requests which will be processed by XML parser. An attacker can use a XML external entity vulnerability for getting unauthorised access to OS filesystem. and another vectors. Install this SAP Security Note to prevent the risks. CVSS v3 Base Score: 8.3 / 10
- A Missing Authentication check vulnerability in SAP NetWeaver System Landscape Directory (2565622): An attacker can use Missing authorization check vulnerability for access to a service without any authorization procedures and use service functionality that has restricted access. This can lead to an information disclosure, privilege escalation and other attacks. CVSS v3 Base Score: 8.3 / 10
- SAP HANA Extended Application Services has an Security vulnerabilities (2525222): An attacker can use Information disclosure vulnerability for revealing additional information (system data, debugging information, etc) which will help to learn about a system and to plan other attacks. Up to 7 different vulnerabilities has been referenced (CVE), however a total of 8 vulnerabilities are related according to the report from the company who found the issues. Install this SAP Security Note to prevent the risks. CVSS v3 Base Score: 7.1 / 10
- SQL-injection vulnerability in the component BC-UPG (1584573 and 1977547): These notes are a re-release of an old note published as far back as 2011. It concerns an SQL-injection vulnerability in the component BC-UPG. The latter mentioned note is auxiliary to the first, in that it supplements correction instructions for it. It was also released before, in 2014. The supplement is only relevant for newly installed systems, or systems which have never been changed using Software Update Manager 1.0 or 2.0 in the years since the first note was created. SAP found that the correction instructions were not fitting in all situations, which led to the creation of the auxiliary note. We advise you to take this opportunity to review the necessity of the note for your specific situation. CVSS v3 Base Score: Check SAP Portal (High and therefore >= 7 / 10)
- Open Source Software Security Vulnerabilities in SAP Internet Graphics Server (IGS)” (2538829): Depending on the vulnerability (again 3 different CVEs are referenced), attackers can exploit a Denial of service vulnerability for terminating a process of vulnerable component. Nobody can use this service. This fact has a negative influence on business processes and business reputation as result. In the note, SAP addresses vulnerabilities in libtiff, giflib and libpng, all of which are third-party open source libraries which handle images (TIFF, GIF and PNG, respectively). The vulnerabilities in these libraries have been around for over a decade. Install this SAP Security Note to prevent the risks. CVSS v3 Base Score: 8.8 / 10
- Potential Information Disclosure in SAP HANA Capture & Replay Trace File (2587369): An attacker can use an Information disclosure vulnerability to learn about a system and to plan other attacks. This note addresses credentials that are stored in clear text in the indexserver trace files of a system using the optional capture & replay functionality of SAP HANA. An attacker would need to obtain TRACE_ADMIN or CATALOG READ authorization to display the indexserver trace files. Besides updating the software to later versions, two manual workarounds are provided to immediately eliminate the threat. CVSS v3 Base Score: 7.6 / 10
- Information Disclosure vulnerability in SAP BPA BY REDWOOD (2596535): An attacker can use it to reveal additional information (e.g. system data, debugging information, etc.) that aids in learning about a system and planning more severe attacks. CVSS v3 Base Score: 7.5 / 10
- Denial of Service (DOS) in GWJPO (2604541): Here we see another example of a vulnerable third-party open source library ending up causing a security flaw in SAP. In this case, the vulnerable software is Apache CXF; an open source services framework helping developers build services using frontend programming APIs like JAX-WS and JAX-RS. GWJPO is using a particular vulnerable CXF servlet, which allows an attacker to prevent legitimate users from accessing a service, either by crashing or flooding the service. CVSS v3 Base Score: Check SAP Portal (High and therefore >= 7 / 10)
- SQL Injection Vulnerability in FI-LOC-FI-RU (2331141): User input was not sufficiently screened and sanitized by this component; therefore it was possible for users to submit improper data and inject dangerous SQL-statements, exposing the backend database and its sensitive content. CVSS v3 Base Score: Check SAP Portal (High and therefore >= 7 / 10)
- Cross-Site Scripting (XSS) Vulnerability in SAP CRM WebClient UI (2595262): It’s not uncommon for an XSS vulnerability to be found in the SAP CRM WebClient UI. This note seems to acknowledge that fact by referencing previously released SAP notes concerning XSS in the CRM Webclient UI. The difference is that this one is of a more critical nature then others reported before. The referenced notes are required to be patched as a prerequisite. CVSS v3 Base Score: Check SAP Portal (High and therefore >= 7 / 10)