Inprosec a través de sus servicios, como el SAP Security Assessment, ayuda a sus clientes a mejorar los niveles de seguridad de sus sistemas SAP.
Notas Noviembre 2022
Resumen y highlights del Mes
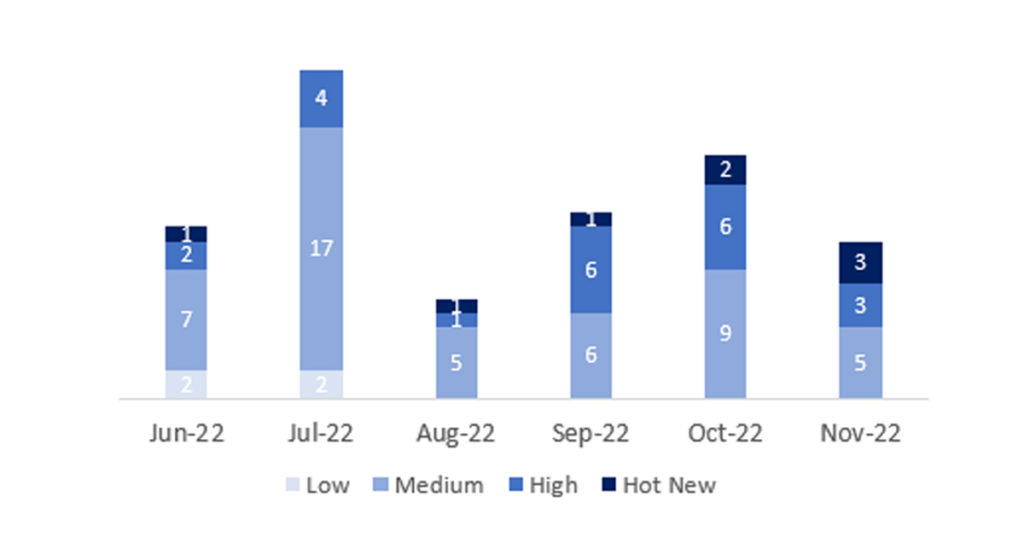
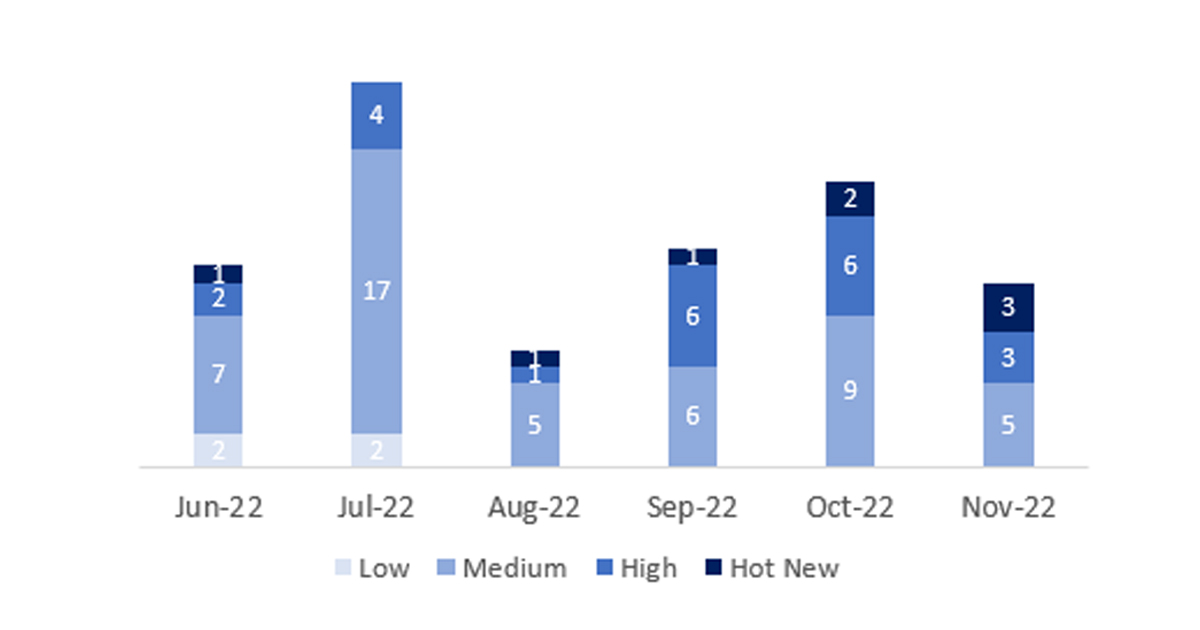
El número total de notas/parches ha sido de 14, 8 menos que el mes pasado. El número de Hot News aumenta, pasando de 2 a 4 en este mes. Por otro lado, cabe destacar que el número de notas de criticidad alta disminuye este mes pasando de 6 a 3. Como siempre dejaremos las notas medias y bajas sin revisar en este mes, pero daremos detalle de un total de 7 notas (todas las que tengan un CVSS de 7 o mayor).
Tenemos un total de 14 notas para todo el mes (las 11 del patch Tuesday, 9 nuevas y 2 actualizaciones, son 6 notas menos que el pasado mes).
Revisaremos en detalle 7 del total de 7 notas altas y HotNews, 2 de las 4 HotNews son nuevas y 5 de 6 notas altas serían nuevas (aquellas de CVSS mayor o igual a 7).
- La nota más crítica del mes (con CVSS 10) es la habitual nota relacionada con «Google Chromium».
- La siguiente en criticidad (CVSS 9,9) sería otra HotNews, relacionada con “Insecure Deserialization of Untrusted Data in SAP BusinessObjects Business Intelligence Platform (Central Management Console and BI Launchpad)”
- La siguiente en criticidad (CVSS 9,8) otra HotNews, referida a “Multiple Vulnerabilities in SQlite bundled with SAPUI5”
- La siguiente se trata de otra HotNews (CVSS 9,6), es una actualización de la nota relacionada con “Account hijacking through URL Redirection vulnerability in SAP Commerce login form”
- La siguientes en criticidad (CVSS 8,7, 8,1, y 7,0) son tres notas altas, una de » Multiple vulnerabilities in SAP NetWeaver Application Server ABAP and ABAP Platform”, la siguiente es una actualización de una nota lanzada en Julio, “Privilege escalation vulnerability in SAP SuccessFactors attachment API for Mobile Application(Android & iOS)” y la última estaría relacionada con “Arbitrary Code Execution vulnerability in SAP 3D Visual Enterprise Author and SAP 3D Visual Enterprise Viewer” .
- Este mes el tipo más predominante es “Cross-Site Scripting (XSS)” (2/14 y 1/11 en patch day).
Detalle completo
El detalle completo de las notas más relevantes es el siguiente (en inglés):
- Update – Security updates for the browser control Google Chromium delivered with SAP Business Client (2622660): This security note addresses multiple vulnerabilities in the 3rd party web browser control Chromium, which can be used within SAP Business Client. This note will be modified periodically based on web browser updates by the open source project Chromium. The note priority is based on the highest CVSS score of all the vulnerabilities fixed in the latest browser release. If the SAP Business Client release is not updated to the latest patch level, displaying web pages in SAP Business Client via this open source browser control might lead to different vulnerabilities like memory corruption, Information Disclosure and the like. The solution will be to update the SAP Business Client patch to the newest one, which contains the most current stable major release of the Chromium browser control, which passed the SAP internal quality measurements of SAP Business Client. CVSS v3 Base Score: 10 / 10 (Multiple CVE´s).
- Insecure Deserialization of Untrusted Data in SAP BusinessObjects Business Intelligence Platform (Central Management Console and BI Launchpad) (3243924): There is no verification in the de-serialization process, in some workflow of SAP BusinessObjects BI Platform (Central Management Console and BI LaunchPad), an authenticated attacker with low privileges can intercept a serialized object in the parameters and substitute with malicious serialized one, which leads to deserialization of untrusted data vulnerability. CVSS v3 Base Score: 9,9 / 10 [CVE-2022-41203].
- Multiple Vulnerabilities in SQlite bundled with SAPUI5 (3249990): An issue was found in fts5UnicodeTokenize() in ext/fts5/fts5_tokenize.c in Sqlite. A unicode61 tokenizer configured to treat unicode «control-characters» (class Cc), was treating embedded nul characters as tokens. SAPUI5 framework is using SQLite < 3.34.0 which was treating null characters as tokens, this could be exploited by an user over the network having low privileges leading to considerable impact on confidentiality, integrity and availability of applications using SAPUI5. . CVSS v3 Base Score: 9,8 / 10 [CVE-2021-20223].
- Update – Account hijacking through URL Redirection vulnerability in SAP Commerce login form( 3239152): An attacker can change the content of an SAP Commerce login page through a manipulated URL. They can inject code that allows them to redirect submissions from the affected login form to their own server. This allows them to steal credentials and hijack accounts. A successful attack could compromise the Confidentiality, Integrity, and Availability of the system. This is due to multiple URLs on the SAP Commerce OAuth extension login page not being sanitized. This allowed attackers to construct manipulated URLs to the login page that would change the behaviour of the login form. In particular, login credentials would be redirected from the SAP Commerce server to an arbitrary server on the Internet. CVSS v3.0 Base Score: 9,6 / 10 [CVE-2022-41204]
- Multiple vulnerabilities in SAP NetWeaver Application Server ABAP and ABAP Platform (3256571): Due to insufficient input validation, SAP NetWeaver Application Server ABAP and ABAP Platform allows an attacker with high level privileges to use a remote enabled function to delete a file which is otherwise restricted. On successful exploitation an attacker can completely compromise the integrity and availability of the application. CVSS v3 Base Score: 8,7 / 10 (CVE-2022-41214).
- Update – Privilege escalation vulnerability in SAP SuccessFactors attachmentAPIfor Mobile Application(Android &iOS) (3226411): Due to misconfigured application endpoints, SAP SuccessFactors attachment APIs allow an attacker with user privileges to perform activities with admin privileges over the network. These APIs were consumed in the SF Mobile application for Time Off, Time Sheet, EC Workflow and Benefits. On successful exploitation, the attacker can read/write attachments, compromising the confidentiality and integrity of the application. Customers using attachments in Time Off, Time Sheet, EC Workflow and Benefits modules of SAP SF Mobile Application are impacted. Several measures have been taken to resolve the identified vulnerability in the most recent software update. This vulnerability impacts users who are using the iOS and Android mobile application versions released previous to V8.0.5. For this reason, the SAP SuccessFactors mobile team is releasing an immediate fix to stop the ability to download, upload or preview attachments from the impacted SAP SF Mobile modules at this time. To fix the issue, download the latest version of the SAP SuccessFactors iOS and Android mobile application (V8.0.5) to ensure the organization is not at risk of any threats from this vulnerability. CVSS v3 Base Score: 8,1 / 10 (CVE-2022-35291).
- Arbitrary Code Execution vulnerability in SAP 3D Visual Enterprise Author and SAP 3D Visual Enterprise Viewer (3263436): SAP SQL Anywhere and SAP IQ database servers are vulnerable to a remote unauthenticated stack-based buffer overflow when the server is running with a server debugging option. Impacts of stack-based buffer overflow are, read and modify unauthorized data. Vulnerability has a direct impact on availability of a system. CVSS v3 Base Score: 7.0 / 10 [CVE-2022-41211]
Enlaces de referencia
Otras referencias, en inglés de SAP y Onapsis (noviembre):
https://dam.sap.com/mac/app/e/pdf/preview/embed/ucQrx6G?ltr=a&rc=10
SAP Patch Day: November 2022 (onapsis.com)
Recursos afectados
El listado completo de los sistemas/componentes afectados es el siguiente:
- SAP 3D Visual Enterprise Author,Version –9.0
- SAP 3D Visual Enterprise Viewer,Version –9.0
- SAP BusinessObjects Business Intelligence Platform (Central Management Console and BI Launchpad), Versions -4.2, 4.3
- SAP Commerce, Versions -1905, 2005, 2105, 2011, 2205
- SAP NetWeaver Application Server ABAP and ABAP Platform,Versions-700, 731, 804, 740, 750, 789
- SAP SuccessFactors attachmentAPIfor Mobile Application(Android &iOS), Versions -<8.1.2
- SAPUI5 CLIENT RUNTIME, Versions –600, 700, 800, 900, 1000
- SAPUI5, Versions –754, 755, 756, 757