Inprosec a través de sus servicios, como el SAP Security Assessment, ayuda a sus clientes a mejorar los niveles de seguridad de sus sistemas SAP.
Notas Enero 2021
Resumen y highlights del Mes
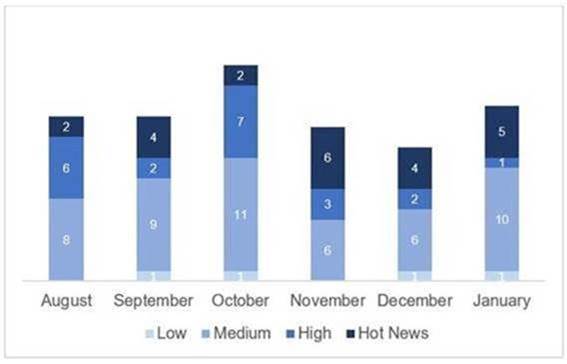
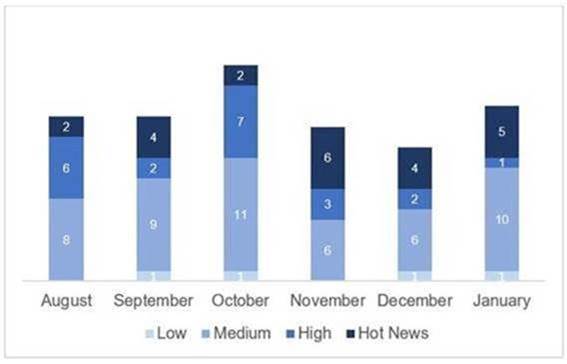
El número total de notas/parches ha aumentado con respecto al último mes. Además de esta subida en el número de notas totales, el número de Hot News también aumenta, siendo 4 las que encontrábamos el mes pasado con respecto a las 5 existentes en Enero. Por otro lado, cabe destacar, que se mantiene el número de notas de criticidad alta siendo 2 tanto el pasado mes como el actual. Como siempre dejaremos las notas medias y bajas sin revisar en este mes, pero daremos detalle de un total de 7 notas (todas las que tengan un CVSS de 7 o mayor).
Tenemos un total de 19 notas para todo el mes, 5 más que el pasado Diciembre (17 del patch Tuesday, 10 nuevas y 7 actualizaciones, siendo 4 más que el pasado mes).
Tenemos 2 notas críticas (Hot News) nuevas, siendo el total de 5 en este mes que destacan por su alto CVVS, una de ellas la actualización recurrente para el SAP Business Client con Chromium . Además revisaremos en detalle 2 del total de 2 notas altas (aquellas de CVSS mayor o igual a 7), ambas notas nuevas.
- La nota más crítica del mes (con CVSS 10) es la recurrente actualización de “Browser Control Chromium Delivered with SAP Business Client (2622660)” que pasa de un CVSS de 9,8 a 10 causado por un fallo crítico (CVE-2020-15967) en el componente de pagos de Chrome.
- Las siguientes 2 notas en criticidad (CVSS 9.9) son dos notas nuevas, una que afecta a SAP Business Warehouse (Database Interface) en múltiples vulnerabilidades y la otra que afecta a Code Injection en SAP Business Warehouse and SAP BW/4HANA.
- A partir de ahí, localizamos 2 Hot News más, ambas actualizaciones, y 2 notas de criticidad alta (high priority) siendo la más relevante con un CVSS de 8.9 una nota nueva de “Information Disclosure in Central Order”. El resto (12) son de nivel medio y bajo, y no las veremos en detalle.
- Este mes los tipos más predominantes son “Missing Authorization Check “(4/19 y 4/17 en patch day), “Cross-Site Scripting (XSS)” (2/19 y 1*/17 en patch day) y “Code Injection” (2/19 y 2/17 en patch day).
En la gráfica (post Enero 2021 de SAP) podemos ver la clasificación de las notas de Enero además de la evolución y clasificación de los últimos 5 meses anteriores (solo las notas del Sec. Tuesday / Patch Day – by SAP):
Detalle completo
El detalle completo de las notas más relevantes es el siguiente (en inglés):
- Update – Security updates for the browser control Google Chromium delivered with SAP Business Client (2622660): This security note addresses multiple vulnerabilities in the 3rd party web browser control Chromium, which can be used within SAP Business Client. This note will be modified periodically based on web browser updates by the open-source project Chromium. From SAP Business Client 6.5 PL5 and above you can use the browser control Chromium for displaying HTML content within SAP Business Client. As this full browser control is delivered and can be installed with SAP Business Client, security corrections for this browser control are shipped with SAP Business Client patches. If the SAP Business Client release is not updated to the latest patch level, displaying web pages in SAP Business Client via this open-source browser control might lead to different vulnerabilities like memory corruption, Information Disclosure and the like. Some well-known impact of those vulnerabilities are: system information disclosure or system crash in worst cases; vulnerabilities might have direct impact on confidentiality, integrity and availability of a system; information gathered can be used to craft further attacks, possibly with more severe consequences. The related CVSS score is always based on the all-time high of all fixed vulnerabilities. While this value didn’t change for more than a year, it has increased now with the newest patch from 9.8 to 10. The increase seems to be caused by a critical flaw (CVE-2020-15967) in Chrome’s payments component. Following Google’s information, the flaw is a use-after-free vulnerability. Use-after-free is a memory-corruption flaw where an attempt is made to access memory after it has been freed. This can cause various malicious impacts, from causing a program to crash, to potentially leading to execution of arbitrary code. CVSS v3 Base Score: 10 / 10.
- Multiple vulnerabilities in SAP Business Warehouse (Database Interface) (2986980): It patches a SQL Injection vulnerability, tagged with CVSS score of 9.9, and a Missing Authorization Check vulnerability, tagged with CVSS score of 6.5. Both vulnerabilities were found in the Database Interface of SAP BW. An improper sanitization of provided SQL commands allowed an attacker to execute arbitrary SQL commands on the database which could lead to a full compromise of the affected system. The Missing Authorization Check vulnerability that was fixed with note #2986980 could lead to an escalation of privileges allowing an attacker to read out any database table. SAP has solved the issue by just disabling the function module. Attention: This will cause a dump in any application that calls this function module! So, it is highly recommended to check your custom code before applying the patch. If the function module is still in use, it is also strongly recommended to think about an alternative “as it must not be used anymore” and to implement the patch. Based on that statement, there is a high chance that the dangerous function module will be removed anyway with one of the next updates. CVSS v3 Base Score: 9.9 / 10 (CVE-2021-21465)
- Code Injection in SAP Business Warehouse and SAP BW/4HANA (2999854): It patches a typical source for this kind of vulnerability. An insufficient input validation could allow a low privileged user to inject malicious code that is stored persistently as a report. This report could be executed afterward, and thus, could potentially lead to scenarios with a high negative impact on the confidentiality, integrity and availability of the affected system (and maybe also of connected systems). Fortunately, the provided patch can be applied automatically via transaction SNOTE and does not require any manual pre or post activities. CVSS v3 Base Score: 9.9 / 10 (CVE-2021-21466)
- Update – Code Injection vulnerability in SAP Business Warehouse (Master Data Management) and SAP BW4HANA (2983367): SAP BW Master Data Management and SAP BW4HANA allows an attacker with high privileges ability to submit a crafted request to generate and execute code without requiring any user interaction. These malicious requests could result in the execution of operating system commands that may completely compromise the confidentiality, integrity and availability of the server and any data or other applications running on it. Reason and Prerequisites: Misuse of a delivered function with the intention to execute arbitrary reports in the system. CVSS v3 Base Score: 9.1 / 10 (CVE-2020-26838)
- Update – Privilege escalation in SAP NetWeaver Application Server for Java (UDDI Server) (2979062): The UDDI Server of SAP NetWeaver Application Server for Java allows an attacker to execute arbitrary OS commands without having the required permissions, known as escalation of privileges vulnerability. Potential impact is total compromise of confidentiality, integrity and availability of server OS. CVSS v3 Base Score: 9.1 / 10 (CVE-2020-26820).
- Information Disclosure in Central Order (3001373): fixes an issue in the binding process of the Central Order service to a Cloud Foundry application that existed before December 4, 2020. This issue allowed unauthorized SAP employees to access the binding credentials of the service. It can be solved by simply deleting and recreating the service instance. If additional service keys were created for the service instance, they need to be recreated, in order to generate new credentials. CVSS v3 Base Score: 8.9 / 10.
- Denial of service (DOS) in SAP NetWeaver AS ABAP and ABAP Platform (3000306): It patches a scenario in SAP NetWeaver AS and ABAP Platform that could lead to a Denial-of-Service experience for the users. Starting the demo examples that are embedded in ABAP Server’s and ABAP Platform’s ABAP Keyword Documentation via the web version allows an unauthenticated attacker to prevent legitimate users from accessing a service, either by crashing or flooding the service. The provided fix prevents the demo examples from being started in parallel. CVSS v3 Base Score: 7.5 / 10 (CVE-2021-21446).
Enlaces de referencia
Enlaces de referencia del CERT del INCIBE en relación a la publicación de las notas para el mes de Enero:
https://www.incibe-cert.es/alerta-temprana/avisos-seguridad/actualizacion-seguridad-sap-enero-2021
Otras referencias, en inglés de SAP y Onapsis (Enero):
https://wiki.scn.sap.com/wiki/pages/viewpage.action?pageId=564760476
https://onapsis.com/blog/sap-security-notes-january-2021
Recursos afectados
- Automated Note Search Tool (SAP Basis), versiones 7.0, 7.01,7.02, 7.31, 7.4, 7.5, 7.51, 7.52, 7.53 y 7.54;
- SAP 3D Visual Enterprise Viewer, versión 9.0;
- SAP Banking Services (Generic Market Data), versiones 400, 450 y 500;
- SAP Business Client, versión 6.5;
- SAP Business Warehouse, versiones 700, 701, 702, 710, 711, 730, 731, 740, 750, 751, 752, 753, 754, 755 y 782;
- SAP BusinessObjects Business Intelligence platform (Web Intelligence HTML interface), versiones 410 y 420;
- SAP BW4HANA, versiones 100 y 200;
- SAP Commerce Cloud, versiones 1808, 1811, 1905, 2005 y 2011;
- SAP EPM ADD-IN, versiones 2.8 y 1010;
- SAP GUI FOR WINDOWS, versión 7.60;
- SAP Master Data Governance, versiones 748, 749, 750, 751, 752, 800, 801, 802, 803 y 804;
- SAP NetWeaver AS JAVA, versiones:
- AS Java (HTTP Service), versiones 7.10, 7.11, 7.20, 7.30, 7.31, 7.40 y 7.50;
- AS JAVA (Key Storage Service), versiones 7.10, 7.11, 7.20 ,7.30, 7.31, 7.40 y 7.50;
- AS JAVA, versiones 7.20, 7.30, 7.31, 7.40 y 7.50;
- SAP NetWeaver Master Data Management, versiones 7.10, 7.10.750 y 710;