Inprosec a través de sus servicios, como el SAP Security Assessment, ayuda a sus clientes a mejorar los niveles de seguridad de sus sistemas SAP.
Hoy os traemos la actualización de las notas de seguridad de SAP, del Q3 de 2020. Aunque se ha producido una gran bajada en el número de notas publicadas (ya que el trimestre pasado había sido el máximo histórico hasta la fecha), seguimos teniendo un número significativo de notas críticas y además en el mismo trimestre coincide que tenemos dos notas nuevas de máxima criticidad (CVSS 10). Destacar, que al menos una de ellas os podría afectar, ya que precisamente es para SAP Solution Manager.
Notas Q3 2020
Resumen y highlights del Trimestre
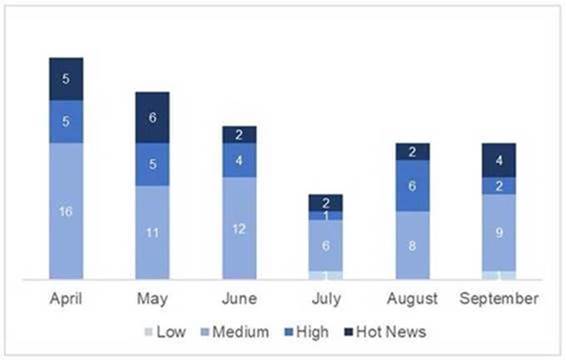
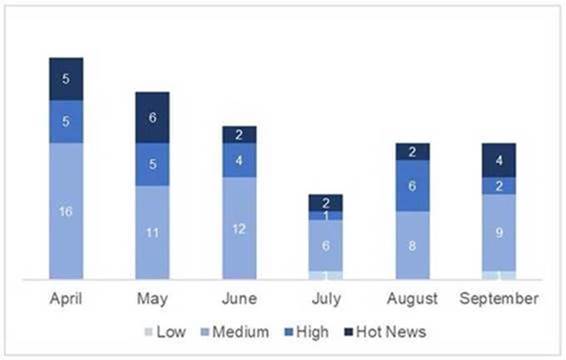
El número total de notas/parches ha disminuido con respecto al último trimestre. También disminuye el número de notas críticas y altas. A excepción del trimestre pasado, donde no encontrábamos ninguna nota baja, éstas sí están presentes en este trimestre. Como siempre dejaremos las notas medias y bajas sin revisar en este trimestre, pero daremos detalle de un total de 15 notas (todas las que tengan un CVSS de 7 o mayor). Como adelatábamos, si destaca que las notas críticas, son especialmente de muy alto nivel (CVSS).
Tenemos 6 notas críticas (Hot News) únicas, siendo el total de 8 en este trimestre, una de ellas la actualización recurrente para el SAP Business Client con Chromium con 2 apariciones y una crítica de SAP NetWeaver AS JAVA (LM Configuration Wizard) que aparece en Julio y se actualiza en Agosto. Además revisaremos en detalle 9 del total de 9 notas altas (aquellas de CVSS mayor o igual a 7) para la revisión en detalle de 15 notas distintas.
- Las notas más crítica del trimestre (ambas con CVSS 10) una relacionada con múltiples vulnerabilidades en SAP NetWeaver AS JAVA (LM Configuration Wizard) y la otra el update que afecta a la falta de verificación de autentificación en SAP Solution Manager.
- Las siguientes en criticidad (CVSS 9.8) son 2. Es la habitual “Browser Control Chromium Delivered with SAP Business Client (2622660)” que aparece 2 veces en este trimestre, la primera vez en julio y posteriormente en septiembre.
- A partir de ahí, tenemos una crítica con CVSS de 9.6, otra con 9.1 y la última con un CVSS de 9.
- De las de nivel alto quizás debamos destacar que existen 2 para para SAP NetWeaver (ABAP) and ABAP Platform, la nota principal y el update con CVSS de 8.3.
Tenemos un total de 61 notas para todo el trimestre, 20 menos que el pasado trimestre (42 de los patch Tuesday, 24 menos que el pasado trimestre):
- En Julio se han publicado un total de 20 notas (10 en el Security Notes Tuesday – 8 nuevas y 2 actualizaciones de notas anteriores).
- Además tenemos un total de 2 “hot news” (críticas). Una que afecta a SAP NetWeaver AS JAVA (LM Configuration Wizard), debido a varias vulnerabilidades, y la segunda, que es un update que se vuelve a repetir para “Browser Control Chromium Delivered with SAP Business Client (2622660)”. Las dos con un CVSS a tener en cuenta de de 10 y 9.8 respectivamente.
- Existe también 2 notas de criticidad alta (high priority), una que afecta a SAP NetWeaver (XMLToolkit for Java) con un CVSS de 7.7 y la otra, la cual es un update que afecta a la divulgación de información en SAP ABAP Server con un CVSS de 7.4. El resto (16) son de nivel medio y bajo, y no las veremos en detalle aunque cabe destacar que 3 de nivel medio afectan a SAP Business Objects.
- Este mes los tipos más predominantes son “Missing Authorization Check” (6/20 y 0/10 en patch day) y “Cross-Site Scripting (XSS)” (4/20 y 4/10 en patch day).
- En Agosto se han publicado un total de 21 notas (16 en el Security Notes Tuesday – 15 nuevas y 1 actualización de notas anteriores).
- Tenemos un total de 2 “hot news” (críticas), 1 nueva, que estaría relacionada con el tipo “Cross-Site Scripting (XSS)” y 1 actualización de la nota que veíamos en el mes de julio “Multiple Vulnerabilities in SAP NetWeaver AS JAVA (LM Configuration Wizard)”. El mismo número de notas críticas que el mes pasado, siendo de igual forma 1 nueva y 1 actualizada.
- Existen también 6 notas de criticidad alta (high priority), la más relevante con un CVSS de 8.5, que mediante acceso no autenticado de un atacante al servidor, permite obtener el nombre de usuario y contraseña de usuarios conectados. El resto de notas (13) son de menor nivel – mayoritariamente nivel medio – y la plataforma destacada este mes es SAP Netweaver, con un total de 7 notas (2 críticas, 3 altas y 2 medias).
- Este mes los tipos más predominantes son “Information Disclosure” (5/21 y 4/16 en patch day) y en segundo lugar empatados “Cross-Site Scripting (XSS)” (4/21 y 3/16 en patch day) y “Missing Authorization Check” (4/21 y 4/16 en patch day).
- En Septiembre se han publicado un total de 20 notas (16 en el Security Notes Tuesday – 10 nuevas y 6 actualizaciones de una nota anterior).
- Tenemos un total de 4 “hot news” (críticas), dos de update y dos nuevas. Siendo las de update, una debido a la falta de verificación de autentificación que afecta a SAP Solution Manager y la otra para el clásico “Browser Control Chromium Delivered with SAP Business Client (2622660)”. Las dos con un CVSS a tener en cuenta de de 10 y 9.8 respectivamente. Con respecto a las dos nuevas, encontramos una que afecta a SAP Marketing debido al control de acceso inadecuado, y otra de vulnerabilidad de código en SAP NetWeaver (ABAP Server) and ABAP Platform. Las dos con un CVSS a tener en cuenta de de 9.6 y 9.1 respectivamente.
- Existen también 2 notas de criticidad alta (high priority), siendo la más relevante un update también para SAP NetWeaver (ABAP) and ABAP Platform con un CVSS de 8.3. La segunda, también update con un CVSS de 7.6, afectaría a SAP NetWeaver AS ABAP debido a la vulnerabilidad de falsificación de solicitudes.
- Este mes los tipos más predominantes son “Cross-Site Scripting (XSS)” (5/20 y 4*/16 en patch day) y “Missing Authorization Check” (4/20 y 2*/16 en patch day).
En la gráfica (post Septiembre 2020 de SAP) podemos ver la evolución y clasificación de las notas de los 3 meses del segundo trimestre del año (2020), además de los 3 meses del pasado trimestre (solo las notas del Sec. Tuesday / Patch Day – by SAP):
Detalle completo
El detalle completo de las notas más relevantes es el siguiente (en inglés):
- Multiple Vulnerabilities in SAP NetWeaver AS JAVA (LM Configuration Wizard) (2934135): This SAP security note addresses vulnerabilities identified in LM Configuration Wizard of SAP NetWeaver AS JAVA. 1- Missing Authentication vulnerability: LM Configuration Wizard of SAP NetWeaver AS JAVA, does not perform an authentication check which allows an attacker without prior authentication, to execute configuration tasks to perform critical actions against the SAP Java system, including the ability to create an administrative user, and therefore compromising Confidentiality, Integrity and Availability of the system. 2- Path Traversal: The insufficient input path validation of certain parameter in the web service, allows an unauthenticated attacker to exploit a method to download zip files to a specific directory. The solution: Authentication and authorization is enforced by code correction. We recommend to apply the patch immediately. If you cannot apply the patch, then at least disable the application aliases as described in the Note 2939665. The Note 2939665 is a workaround and a defense in depth, but not a solution. We recommend disabling the application aliases unless needed. These application aliases are required for a few SAP Lifecycle procedures only, such as the initial technical setup. It is not needed for a day-to-day operations. You can temporarily re-enable these application aliases for executing the SAP lifecycle procedures. CVSS v3 Base Score: 10 / 10 (CVE-2020-6287).
- Update – Security Updates for the Browser Control Chromium Delivered with SAP Business Client (2622660): This note addresses multiple vulnerabilities in the third-party web browser control Chromium, which is used in SAP Business Client and is periodically updated based on web browser updates. Since exploits for third-party tools are more common than exploits that are SAP-specific, which tend to be more targeted and selective, it is important to keep this note installed with every update to stay secure. These patches provide support for Chromium version 84.0.4147.105. CVSS v3 Base Score: 9.8 / 10
- Information Disclosure in SAP NetWeaver (XMLToolkit for Java) (2932473): fixes a bug in the SAP XML Toolkit for Java that allows attackers to access arbitrary files which would otherwise be restricted. Such information can be used afterwards to start further exploits. CVSS v3 Base Score: 7.7 / 10 (CVE-2020-6285).
- Update – Information Disclosure in SAP ABAP Server (2734580): ABAP Server has a weakness in Internet Communication Framework’s logon procedure, which enables a malicious user to steal logon credentials of another user by providing a malicious URL. Please implement the Support Package mentioned in this SAP Note, or the respective correction instruction. The logon procedure is hardened. CVSS v3 Base Score: 7.4 / 10 .
- Cross-Site Scripting (XSS) vulnerability in SAP Netweaver (Knowledge Management) (2928635): It patches a Cross-Site Scripting vulnerability that can result in complete compromise of system confidentiality, integrity and availability. Knowledge Management (KM) is a component of SAP NetWeaver, specifically of SAP Enterprise Portal. It is intended as a unified entry point to manage different data sources in various formats and comes by default with every installation of SAP Enterprise Portal. Users can create new content, folders, modify existing ones and upload files to the system. They can upload, by default, files of any type, including html files, which, when read by any other user will be rendered by their browsers. This upload process can be exploited to upload malicious html files with javascript code in it, performing a Stored Cross-Site Scripting (XSS) attack. The exploit is possible as the filtering mechanism that was implemented by SAP in order to prevent uploaded files from being injected with executable scripts did not work properly. CVSS v3 Base Score: 9.0 / 10 (CVE-2020-6284).
- Missing Authentication check in SAP BusinessObjects Business Intelligence Platform (2927956): It patches a vulnerability that allows an attacker with access to the internal network(LAN) to gain unauthenticated access to X server. As a result, the attacker can comprehend keyboard and mouse activities of a user who is connected remotely and can even grab screenshots of the remote host. From this, it is possible to gain access to the user name and password of the connected user. CVSS v3 Base Score: 8.5 / 10 (CVE-2020-6294).
- Missing Authorization check in SAP Banking Services (Generic Market Data) (2939685): It describes a Missing Authorization Check vulnerability in SAP Banking Services. This High Priority Note, tagged with CVSS score 8.3 is strongly recommended for all SAP customers, especially those regulated by GDPR as the vulnerability allows an attacker to read protected Business Partner Generic Market Data (GMD) or to modify the related GMD data key figure values in SAP Banking Services. CVSS v3 Base Score: 8.3 / 10 (CVE-2020-6298).
- Code Injection Vulnerability in SAP NetWeaver (ABAP) and ABAP Platform (2941667): SAP NetWeaver (ABAP Server) and ABAP Platform allows a low privileged attacker to inject code by executing an ABAP report over the network. An attacker could so get access to data, overwrite arbitrary SAP programs including essential logon program and could thereby lead to a Denial of Service. With the corrections in this SAP Note, we move authorization check S_BDC_MONI from SHDB also to RSBDCREC. In addition, we prevent malicious injection of code by a change of the INSERT REPORT behavior using the central API to create development objects. CVSS v3 Base Score: 8.3 / 10 (CVE-2020-6296).
- Missing Authentication check in SAP NetWeaver AS JAVA (2941315): It describes a Missing Authentication Check vulnerability. The vulnerability is exposed by a web service and an exploit can result in a complete denial of service.. CVSS v3 Base Score: 7.5 / 10 (CVE-2020-6309).
- Unrestricted File Upload in SAP NetWeaver (Knowledge Management) (2938162): SAP NetWeaver (Knowledge Management) allows an unauthenticated attacker to upload a file without requiring any user action. This will allow the attacker to access, or modify or make unavailable existing files but the impact is limited to the files themselves and is restricted by other policies such as access control lists and other upload file size restrictions.Reason: By default, an access point not intended for public usage failed to check authentication for file upload operations. Solution:The affected functions have been enforced to properly check access restrictions.Implement the Support Packages and Patches referenced by this SAP Note.. CVSS v3 Base Score: 7.3 / 10 (CVE-2020-6293).
- Information Disclosure in SAP Adaptive Server Enterprise (2941332): It patches an Information Disclosure vulnerability in the installer of the SAP Adaptive Enterprise cockpit. It allows an attacker to read information of the installation log files that can be used afterwards to start further attacks. This issue is fixed in the SAP ASE installer by removing the encrypted information from the installation log file. CVSS v3 Base Score: 7 / 10 (CVE-2020-6295).
- Update – Missing Authentication Check in SAP Solution Manager (2890213). SAP Solution Manager User-Experience Monitoring does not perform any authentication for a service resulting in complete compromise of all SMDAgents connected to the Solution Manager. This issue is relevant for all the customers using SAP Solution Manager 7.2 on Support Package levels less than SP12. The solution enables user authentication on the User-Experience Monitoring administration service and thereby removes the root cause of finding CVE-2020-6207. CVSS v3 Base Score: 10 / 10 (CVE-2020-6207).
- Improper Access Control in SAP Marketing (Mobile Channel Servlet) (2961991): It patches a vulnerability in the Mobile Channel Servlet that allows an authenticated attacker to invoke certain functions that are restricted. An exploit of the vulnerability enables an attacker to perform tasks related to contact and interaction data. As a workaround, if applying the patch is not possible, customers can disable the servlet. CVSS v3 Base Score: 9.6 / 10 (CVE-2020-6320]).
- Code Injection vulnerability in SAP NetWeaver (ABAP Server) and ABAP Platform (2958563): This note provides a patch for a Code Injection vulnerability in the SAP NetWeaver AS ABAP and SAP ABAP Platforms, enabling an attacker to take complete control of the application, including viewing, changing or deleting data by injecting code into the working memory which is subsequently executed by the application. It can also be used to cause a general fault in the application causing it to terminate. It should be mentioned that only ABAP Servers on DB4 or Sybase are vulnerable, that the vulnerability scenario is not relevant to SAP ABAP for Cloud Environment and the described attack cannot be executed in SAP cloud products. CVSS v3 Base Score: 9.1 / 10 (CVE-2020-6318).
- Update – Code Injection Vulnerability in SAP NetWeaver (ABAP) and ABAP Platform (2941667): SAP NetWeaver (ABAP Server) and ABAP Platform allows a low privileged attacker to inject code by executing an ABAP report over the network. An attacker could so get access to data, overwrite arbitrary SAP programs including essential logon program and could thereby lead to a Denial of Service. With the corrections in this SAP Note, we move authorization check S_BDC_MONI from SHDB also to RSBDCREC. In addition, we prevent malicious injection of code by a change of the INSERT REPORT behavior using the central API to create development objects. CVSS v3 Base Score: 8.3 / 10 (CVE-2020-6296)
Enlaces de referencia
Enlaces de referencia del CERT del INCIBE en relación a la publicación de las notas para los 3 meses de este trimestre:
https://www.incibe-cert.es/alerta-temprana/avisos-seguridad/actualizacion-seguridad-sap-julio-2020
https://www.incibe-cert.es/alerta-temprana/avisos-seguridad/actualizacion-seguridad-sap-agosto-2020
Otras referencias, en inglés de SAP y Onapsis (en orden: Julio->Septiembre):
https://wiki.scn.sap.com/wiki/pages/viewpage.action?pageId=552599675
https://onapsis.com/blog/sap-security-notes-july-2020-recon
https://wiki.scn.sap.com/wiki/pages/viewpage.action?pageId=552603345
https://wiki.scn.sap.com/wiki/pages/viewpage.action?pageId=557449700
https://onapsis.com/blog/sap-security-notes-september-2020
Recursos afectados
- BANKING SERVICES FROM SAP 9.0 (Bank Analyzer), versión 500;
- S/4HANA FIN PROD SUBLDGR, versión 100;
- SAP 3D Visual Enterprise Viewer, versión 9;
- SAP Adaptive Server Enterprise, versiones 15.7, 16.0.
- SAP Banking Services (Generic Market Data), versiones 400, 450 y 500;
- SAP Business Client, versión 6.5;
- SAP Business Objects Business Intelligence Platform (BI Workspace), versiones 4.1 y 4.2;
- SAP Business Objects Business Intelligence Platform, versiones 4.1, 4.2 y 4.3.
- SAP Commerce, versiones 6.7, 1808, 1811, 1905 y 2005;
- SAP Data Intelligence, versión 3;
- SAP Disclosure Management, versión 1.0;
- SAP ERP (HCM Travel Management), versiones 600, 602, 603, 604, 605, 606, 607 y 608;
- SAP Marketing (Mobile Channel Servlet), versiones 130, 140 y 150;
- SAP NetWeaver:
- ABAP Server y ABAP Platform, versiones 700, 701, 702, 710, 711, 730, 731, 740, 750, 751, 752, 753, 754 y 755;
- AS ABAP (BSP Test Application), versiones 700, 701, 702, 730, 731, 740, 750, 751, 752, 753, 754 y755;
- AS ABAP, versiones 700, 701, 702, 710, 711, 730, 731, 740, 750, 751, 752, 753 y 754;
- Knowledge Management, versiones 7.30, 7.31, 7.40 y 7.50;
- SAP NetWeaver AS JAVA (P4 Protocol), versiones:
- CORE-TOOLS (IIOP service) versiones 7.10, 7.11, 7.20, 7.30, 7.31, 7.40 y 7.50;
- ENGINEAPI versiones 7.10, 7.11, 7.20, 7.30, 7.31, 7.40, 7.50
- J2EE-FRMW versiones J2EE-FRMW 7.10 y 7.11
- LM Configuration Wizard versiones 7.30, 7.31, 7.40 y 7.50;
- SERVERCOR (IIOP service) versiones 7.10, 7.11, 7.20, 7.30, 7.31, 7.40 y 7.50;
- SERVERCORE versiones 7.10, 7.10 y 7.11;
- WSRM versiones 7.10, 7.11, 7.20, 7.30, 7.31, 7.40 y 7.50;
- SAP S/4 HANA (Fiori UI for General Ledger Accounting), versiones 103 y 104;
- SAP Solution Manager (User Experience Monitoring), versión 7.2;
- SAPFiori (Launchpad), versiones 750, 752, 753, 754 y 755;
- SAPUI5 (SAP_UI), versiones 750, 751, 752, 753, 754 y 755;
- SAPUI5 (UI_700), versión 200;
- SAPUI5 (UISAPUI5_JAVA), versión 7.50;