Inprosec a través de sus servicios, como el SAP Security Assessment, ayuda a sus clientes a mejorar los niveles de seguridad de sus sistemas SAP.
Notas Octubre 2022
Resumen y highlights del Mes
El número total de notas/parches ha sido de 22, 6 más que el mes pasado. El número de Hot News aumenta, pasando de 1 a 2 en este mes. Por otro lado, cabe destacar que el número de notas de criticidad alta se mantiene con un total de 6 este mes, igual que en septiembre. Como siempre dejaremos las notas medias y bajas sin revisar en este mes, pero daremos detalle de un total de 8 notas (todas las que tengan un CVSS de 7 o mayor).
Tenemos un total de 22 notas para todo el mes las mismas que el pasado agosto (las 17 del patch Tuesday, 16 nuevas y 1 actualizaciones, son 4 notas más que el pasado mes).
Revisaremos en detalle 8 del total de 8 notas altas y HotNews, ambas HotNews son nuevas y 5 de 6 notas altas serían nuevas (aquellas de CVSS mayor o igual a 7).
- La nota más crítica del mes (con CVSS 9,9) es una nota relacionada con “File path traversal vulnerability in SAP Manufacturing Execution”
- La siguiente en criticidad (con CVSS 9,6) sería la otra HotNews, relacionada con “Account hijacking through URL Redirection vulnerability in SAP Commerce login form”
- La siguientes en criticidad (CVSS 8,2, 8,2, 8,1, 7,7 , 7,0 y 7,0) son seis notas altas, una de » Information Disclosure vulnerability in SAP BusinessObjects Business Intelligence Platform (Program Objects)”, la siguiente es una actualización de una nota lanzada en agosto, «Information Disclosure vulnerability in SAP BusinessObjects Business Intelligence Platform (Monitoring DB)”, la siguiente con “Buffer Overflow in SAP SQL Anywhere and SAP IQ” , otra estaría relacionada con “Information Disclosure vulnerability in SAP BusinessObjects Business Intelligence Platform(AdminTools/ Query Builder)” en la plataforma SAP Business, otra relacionadacon “Multiple vulnerabilities in SAP 3D Visual Enterprise Viewer” y la última estaría relacionada con “Multiple vulnerabilities in SAP 3D Visual Enterprise Author” .
- Este mes los tipos más predominantes son “Information Disclosure vulnerability» (7/22 y 6/17 en patch day) y “Cross-Site Scripting (XSS)” (4/22 y 2/16 en patch day).
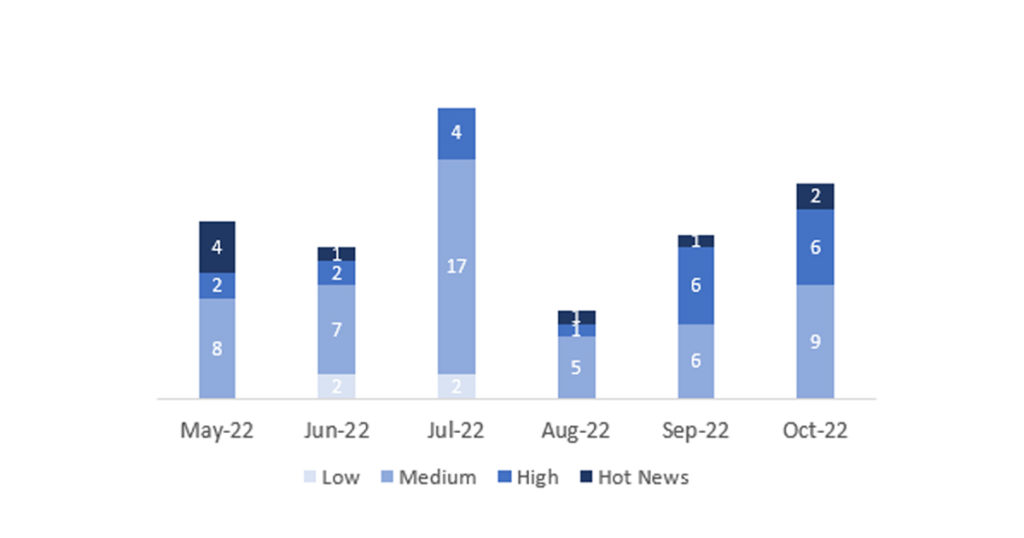
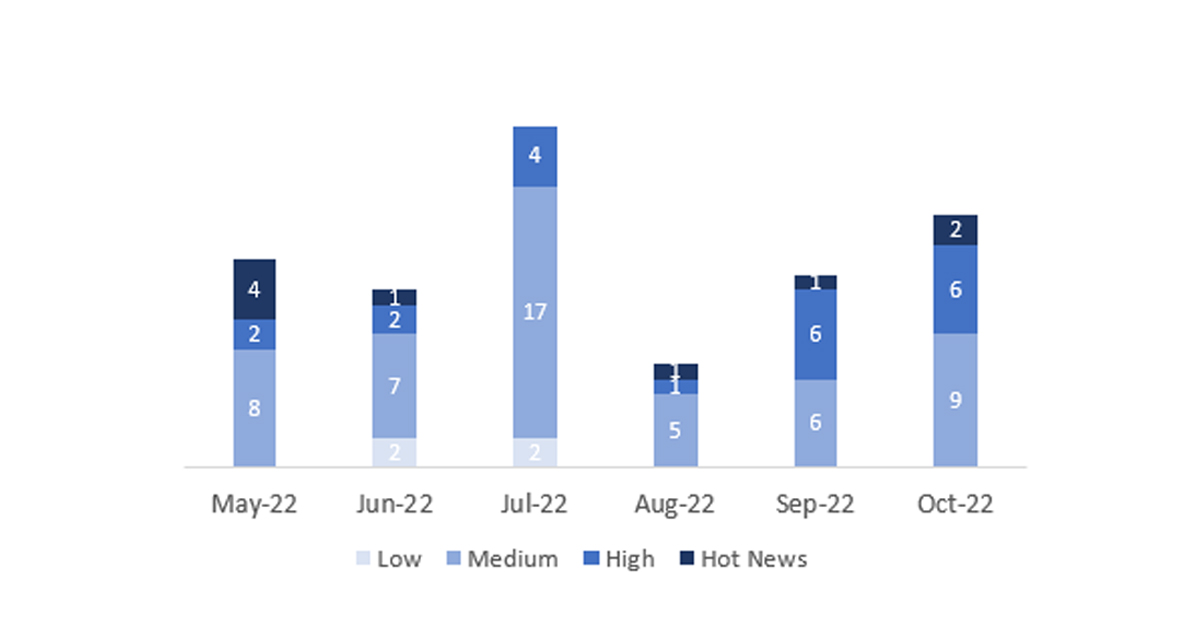
En la gráfica (post octubre 2022 de SAP) podemos ver la clasificación de las notas de octubre además de la evolución y clasificación de los últimos 5 meses anteriores (solo las notas del Sec. Tuesday / Patch Day – by SAP):
Detalle completo
El detalle completo de las notas más relevantes es el siguiente (en inglés):
- File path traversal vulnerability in SAP Manufacturing Execution (3242933): SAP Manufacturing Execution allows an attacker to exploit insufficient validation of a file path request parameter. The intended file path can be manipulated to allow arbitrary traversal of directories on the remote server. The file content within each directory can be read which may lead to information disclosure. CVSS v3 Base Score: 9,9 / 10 [CVE-2022-39802].
- Account hijacking through URL Redirection vulnerability in SAP Commerce login form( 3239152): An attacker can change the content of an SAP Commerce login page through a manipulated URL. They can inject code that allows them to redirect submissions from the affected login form to their own server. This allows them to steal credentials and hijack accounts. A successful attack could compromise the Confidentiality, Integrity, and Availability of the system. This is due to multiple URLs on the SAP Commerce OAuth extension login page not being sanitized. This allowed attackers to construct manipulated URLs to the login page that would change the behavior of the login form. In particular, login credentials would be redirected from the SAP Commerce server to an arbitrary server on the Internet. CVSS v3.0 Base Score: 9,1 / 10 [CVE-2022-41204].
- Information Disclosure vulnerability in SAP BusinessObjects Business Intelligence Platform (Program Objects) (3229132): Under certain conditions an attacker can get access to OS credentials. Attacker must be authenticated, administrator sees credentials in clear text,normal user sees credentials in encrypted form. Getting access to OS credentials enables the attacker to modify system data and make the system unavailable leading to high impact on confidentiality and low impact on integrity and availability of the application. CVSS v3 Base Score: 8,2 / 10 (CVE-2022-35291).
- Update – Information Disclosure vulnerability in SAP BusinessObjects Business Intelligence Platform (MonitoringDB) (3213507): In SAP Business One application when a service is created, the executable path contains spaces and isn’t enclosed within quotes, leading to a vulnerability known as Unquoted Service Path which allows a user to gain SYSTEM privileges. If the service is exploited by adversaries, it can be used to gain privileged permissions on a system or network leading to high impact on Confidentiality, Integrity and Availability. To fix the problem, Customer need upgrade to SAP Business One FP2202HF1. CVSS v3 Base Score: 8,2 / 10 (CVE-2022-35292).
- Buffer Overflow in SAP SQL Anywhere and SAP IQ (3232021): SAP SQL Anywhere and SAP IQ database servers are vulnerable to a remote unauthenticated stack-based buffer overflow when the server is running with a server debugging option. Impacts of stack-based buffer overflow are, read and modify unauthorized data.vulnerability has a direct impact on availability of a system. CVSS v3 Base Score: 8,1 / 10 [CVE-2022-35299].
- Information Disclosure vulnerability in SAP BusinessObjects Business Intelligence Platform(AdminTools/ Query Builder) (3239293): Under certain conditions BOE AdminTools/ BOE SDK allows an attacker to access information which would otherwise be restricted. The note provides a link to knowledge base article 214444559 for the Business Intelligence platform maintenance schedule and strategy. CVSS v3 Base Score: 7.7 / 10 (CVE-2022-39015).
- Multiple vulnerabilities in SAP 3D Visual Enterprise Viewer (3245928): Due to lack of proper memory management, when a victim opens manipulated file received from untrusted sources in SAP 3D Visual Enterprise Viewer, there is a possibility of following attack scenarios being executed arbitrary code execution, 1. Arbitrary Code Execution can be triggered when payload forces re-use of dangling pointer which refers to overwritten space in memory. The accessed memory must be filled with code to execute the attack. Therefore, repeated success is unlikely. Stack-based buffer overflow. Since the memory overwritten is random, based on access rights of the memory, repeated success is not assured., 2. Denial of service, the application crashes and becomes temporarily unavailable to the user until restart of the application. CVSS v3 Base Score: 7.0 / 10 (Multiple´s CVEs).
- Multiple vulnerabilities in SAP 3D Visual Enterprise Author (3245929): Due to lack of proper memory management, when a victim opens manipulated file received from untrusted sources in SAP 3D Visual Enterprise Viewer, there is a possibility of following attack scenarios being executed arbitrary code execution, 1. Arbitrary Code Execution can be triggered when payload forces re-use of dangling pointer which refers to overwritten space in memory. The accessed memory must be filled with code to execute the attack. Therefore, repeated success is unlikely. Stack-based buffer overflow. Since the memory overwritten is random, based on access rights of the memory, repeated success is not assured., 2. Denial of service, the application crashes and becomes temporarily unavailable to the user until restart of the application. CVSS v3 Base Score: 7.0 / 10 (Multiple´s CVEs).
Enlaces de referencia
Otras referencias, en inglés de SAP y Onapsis (octubre):
https://dam.sap.com/mac/app/e/pdf/preview/embed/ucQrx6G?ltr=a&rc=10
https://onapsis.com/blog/sap-security-patch-day-october-2022
Recursos afectados
El listado completo de los sistemas/componentes afectados es el siguiente:
- SAP 3D Visual Enterprise Author, Version -9
- SAP 3D Visual Enterprise Viewer, Version -9
- SAP Business Objects Platform (MonitoringDB), Version -430
- SAP BusinessObjects Business Intelligence Platform (Program Objects),Versions -420, 430
- SAP BusinessObjects Business Intelligence Platform(Admin Tools/Query Builder),Versions–420, 430
- SAP Commerce, Versions -1905, 2005, 2105, 2011, 2205
- SAP IQ, Version -16.1
- SAP Manufacturing Execution, Versions -15.1, 15.2, 15.3
- SAP SQL Anywhere, Version -17.0