Inprosec a través de sus servicios, como el SAP Security Assessment, ayuda a sus clientes a mejorar los niveles de seguridad de sus sistemas SAP.
Notas Agosto 2022
Resumen y highlights del Mes
El número total de notas/parches ha sido de 11, 16 menos que el mes pasado. A pesar de un menor número de notas, el número de Hot News aumentan, no habiendo ninguna el mes pasado, con respecto a la nota existente en este mes de agosto. Por otro lado, cabe destacar que disminuyen el número de notas de criticidad alta pasando de 5 a 3 en este mes. Como siempre dejaremos las notas medias y bajas sin revisar en este mes, pero daremos detalle de un total de 4 notas (todas las que tengan un CVSS de 7 o mayor).
Tenemos un total de 11 notas para todo el mes, 16 notas menos que el pasado Julio (las 7 del patch Tuesday, 5 nuevas y 2 actualizaciones, son 16 notas menos que el pasado mes).
Revisaremos en detalle 4 del total de 4 notas altas y Hot News, siendo la Hot News una actualización de una nota anterior y las 3 notas altas serían nuevas (aquellas de CVSS mayor o igual a 7).
- Las nota más crítica del mes (con CVSS 10) es la habitual nota relacionada con «Google Chromium».
- La siguientes en criticidad (CVSS 8,2, 8,1 y 7,3) son tres notas altas, una de «Information Disclosure vulnerability” en la plataforma SAP BusinessObjects Business Intelligence Platform, otra relacionada con “Privilege escalation vulnerability” en SAP SuccessFactors, y la última estaría relacionada con “Information Disclosure” en la plataforma SAP Landscape Management.
- El resto (7) son de nivel medio y bajo, y no las veremos en detalle.
- Este mes los tipos más predominantes son “Information Disclosure vulnerability» (6/11 y 4/7 en patch day) y “Missing Authorization Check” (3/11 y 1/7 en patch day).
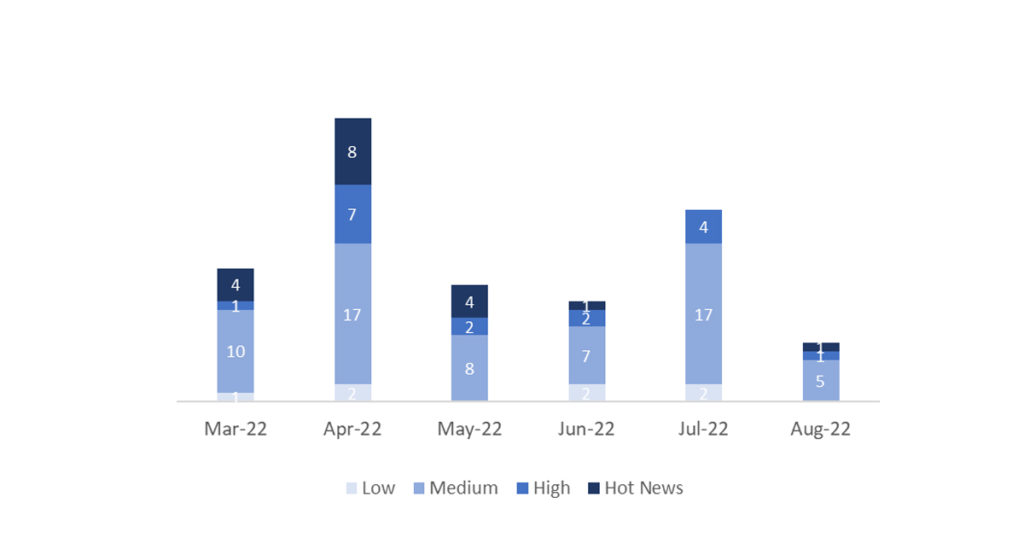
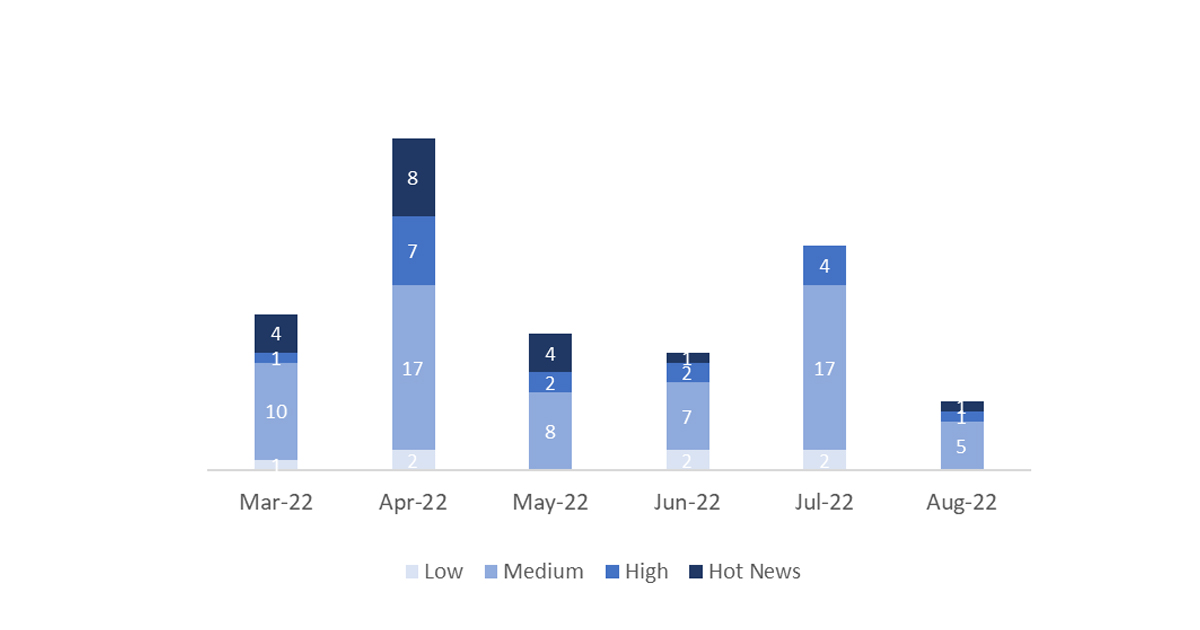
En la gráfica (post agosto 2022 de SAP) podemos ver la clasificación de las notas de agosto además de la evolución y clasificación de los últimos 5 meses anteriores (solo las notas del Sec. Tuesday / Patch Day – by SAP):
Detalle completo
El detalle completo de las notas más relevantes es el siguiente (en inglés):
- Update – Security updates for the browser control Google Chromium delivered with SAP Business Client (2622660): This security note addresses multiple vulnerabilities in the 3rd party web browser control Chromium, which can be used within SAP Business Client. This note will be modified periodically based on web browser updates by the open source project Chromium. The note priority is based on the highest CVSS score of all the vulnerabilities fixed in the latest browser release. If the SAP Business Client release is not updated to the latest patch level, displaying web pages in SAP Business Client via this open source browser control might lead to different vulnerabilities like memory corruption, Information Disclosure and the like. The solution will be to update the SAP Business Client patch to the newest one, which contains the most current stable major release of the Chromium browser control, which passed the SAP internal quality measurements of SAP Business Client. CVSS v3 Base Score: 10 / 10 (Multiple CVE´s).
- Information disclosure vulnerability in SAP BusinessObjects Business Intelligence Platform (Open Document) (3210823): SAP BusinessObjects Open Document allows an unauthenticated attacker to retrieve sensitive information plain text over the network. On successful exploitation, the attacker can view any data available for a business user and put load on the application by an automated attack, completely compromising confidentiality but causing a limited impact on the availability of the application. All versions lower than 4.2 SP9 P6 and 4.3 SP2 are affected by the vulnerability. This issue is fixed in the patches listed in the section «Support Packages & Patches» of the note. CVSS v3 Base Score: 8,2 / 10 (CVE-2022-32245).
- Privilege escalation vulnerability in SAP SuccessFactors attachment API for Mobile Application(Android & iOS) (3226411): Due to misconfigured application endpoints, SAP SuccessFactors attachment APIs allow an attacker with user privileges to perform activities with admin privileges over the network. These APIs were consumed in the SF Mobile application for Time Off, Time Sheet, EC Workflow and Benefits. On successful exploitation, the attacker can read/write attachments, compromising the confidentiality and integrity of the application. Customers using attachments in Time Off, Time Sheet, EC Workflow and Benefits modules of SAP SF Mobile Application are impacted. Several measures have been taken to resolve the identified vulnerability in the most recent software update. This vulnerability impacts users who are using the iOS and Android mobile application versions released previous to V8.0.5. For this reason, the SAP SuccessFactors mobile team is releasing an immediate fix to stop the ability to download, upload or preview attachments from the impacted SAP SF Mobile modules at this time. To fix the issue, download the latest version of the SAP SuccessFactors iOS and Android mobile application (V8.0.5) to ensure the organization is not at risk of any threats from this vulnerability. CVSS v3 Base Score: 8,1 / 10 (CVE-2022-35291).
- Information Disclosure in SAP Landscape Management (3213141): An information Disclosure vulnerability exists in the enterprise edition of SAP Landscape Management that would allow an authenticated user to obtain privileged access to other systems making those other systems vulnerable to information disclosure and modification. The information disclosed are the credentials and it can only be accessed by authenticated SAP Landscape Management users, but they can escalate their privileges to other systems. To fix the problem, the procedure would be as follows: Implement SAP Adaptive Extensions Patch 70, then remove Adaptive Extensions logs from the affected systems, and finally change the affected credentials because the logs could have already been read. CVSS v3 Base Score: 7.3 / 10.
Enlaces de referencia
Otras referencias, en inglés de SAP y Onapsis (agosto):
https://dam.sap.com/mac/app/e/pdf/preview/embed/ucQrx6G?ltr=a&rc=10
https://onapsis.com/blog/sap-security-patch-day-august-2022-sap-businessobjects-focus
Recursos afectados
El listado completo de los sistemas/componentes afectados es el siguiente:
- SAP Authenticator for Android, Versions <1.2.17
- SAP Business Client, Versions 6.5, 7.0, 7.70
- SAP Business Objects Platform (MonitoringDB), Version 430
- SAP BusinessObjects Business Intelligence Platform (CommentaryDB), Versions 420, 430
- SAP BusinessObjects Business Intelligence Platform (Open Document),Versions 420, 430
- SAP Enable Now Manager, Version 1.0
- SAP NetWeaver, Versions 740, 750