As every quarter, we analyze the security notes published by SAP, in this case, we will analyze those of the second quarter of 2018.
We have one critical note (Hot News) in this quarter (published in April and updated in June), an update of a critical note to highlight, and 6 high level notes, to which we will add one Medium note , (he most critical of May for the detailed review of 9 notes)
- The most critical one (CVSS 9.8) is related to the “SAP Business Client” component.
- We also have two critical note updates (one on the previous one and other on CVSS 9.1) and only one high note that goes beyond 8 (CVSS 8.4). The rest of the notes are below this rating.
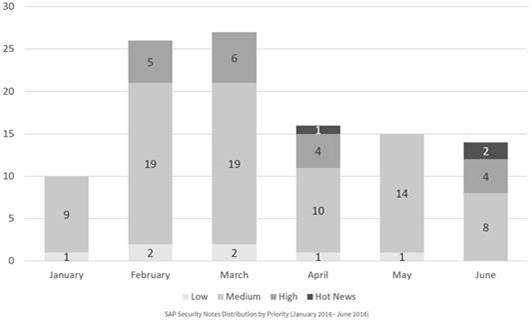
We have a total of 45 notes for the entire quarter, 18 less than quarter, (32 of the Tuesday patches, 1 more than last quarter):
- In April, a total of 16 notes were published (12 in the Security Notes Tuesday – 9 new and 3 updates of previous notes).
- This month we have a “hot new” (critical) with a very high CVSS of 9.8, the highest of the year, related to the “SAP Business Client”.
- This same note receives an update two months later (June). On the other hand, we have 4 high criticality notes (High Priority)
- This month, the most predominant type is “Missing Authorization Check” (4/16 and 1/12 in patch day).
- In May, a total of 15 notes were published (10 on the Security Notes Tuesday – 9 new and 1 updates of previous notes).
- In this month there are no “hot news” (critical) or high criticality (high priority). In fact, except for a low level note, the rest are all of medium level.
- We only detail the note of higher risk / criticality, which has a CVSS of 6.5 related to the component “SAP Internet Graphics Server (IGS)”, which would allow an attacker to load any malicious file. Precisely for this component there are a total of 4 notes of the 15th of the month.
- This month the most predominant types are “Missing Authorization Check” (3/15 and 1/10 in patch day) and “Denial of Service” (3/15 and 3/10 in patch day).
- In June, a total of 14 notes were published (10 in the Security Notes Tuesday – 5 new and 5 updates of previous notes).
- There are no new “hot news” this month, but 2 critical notes are updated (one from April 2018, already mentioned and included in this report). The other updated “Hot News” is November 2016 (2357141) with a CVSS of 9.1.
- There are also a total of 4 of high criticality, all of the Patch Day, being an update of previous note and of the three remaining emphasizing one of SAP Business One with a CVSS of 8.4.
- This month the most predominant types are “Cross-Site Scripting” (3/14 and 1/10 in patch day) and “Remote Command Execution” (3/14 and 1/10 in patch day).
El detalle completo de las notas más relevantes es el siguiente (en inglés):
-
- SAP Business Client has a security vulnerability (2622660): This note bundles multiple vulnerabilities. The bugs concern vulnerabilities in web browser controls that are used to display pages in SAP Business Client 6.5 PL5. Web browser controls are programmable building blocks that software developers use to embed web pages in their applications. Depending on the vulnerability, attackers can exploit a Memory corruption vulnerability for injecting specially crafted code into a working memory which will be executed by the vulnerable application. This can lead to taking complete control of an application, denial of service, command execution and other attacks. This fact has a negative influence on business processes and business reputation as a result. Install this SAP Security Note to prevent the risks. Updated in June 2018 (“If this note has been already implemented, then there is no action required.” Manual steps only have usability impact and no security implications). CVSS v3 Base Score: 9.8 / 10
- SAP Business One has an Denial of Service (DOS) vulnerability (2587985): An attacker can use Denial of service vulnerability for terminating a process of a vulnerable component. For this time nobody can use this service, this fact negatively influences on a business processes, system downtime and business reputation as result. The bug actually exists in Apache, and is introduced by the use of Apache as a HTTP server in the Business One service layer. The bug allows an attacker to cause a segmentation fault by carefully sending a specific sequence of request headers to the server. A segfault happens when a program tries to read or write a memory location it is not supposed to. A segfault will crash the program. In this case, the segfault can be generated due to the absence of sufficient user input validation in the Apache function ap_get_token(). This function is allowed to search past the end of its input string causing a buffer overread. Install this SAP Security Note to prevent the risks. CVSS v3 Base Score: 7.5 / 10
- SAP Visual Composer has a Code Injection vulnerability (2552318): Update a previous Security Note (2376081). Depending on the code, attackers can perform different actions: inject and run their own code, obtain additional information that must be hidden, change or delete data, modify the output of the system, create new users with higher privileges, control the behavior of the system, or can potentially escalate privileges by executing malicious code or even to perform a DOS attack. Install this SAP Security Note to prevent the risks. CVSS v3 Base Score: 7.4 / 10
- Improper Session Management in SAP Business Objects -CMC/BI Launchpad/Fiorified BI Launchpad (2537150): Business Objects (BO or BOBJ) is SAP’s suite of front-end applications which allows customers to effectively process and visualize business intelligence data. The BOBJ vulnerability in this note causes existing user sessions to remain active even after their passwords have been changed. After applying the Support Package Patches mentioned in the note, password changes will be preceded by an alert warning the administrator for the termination of active sessions for the user whose password was changed. On successful password change, active sessions will then be terminated. Updated in June 2018 (“This note will be modified periodically based on web browser updates by respective vendors.” Any time SAP updates this Security Note, you need to do it too.). CVSS v3 Base Score: 7.3 / 10
- SAP Internet Graphics Server (IGS) has a security vulnerability (2615635): An attacker can upload any file, use Cross-site scripting vulnerability for injecting a malicious script into a page. Reflected XSS feature is necessary to trick a user – he or she would make the user follow a specially crafted link. In terms of stored XSS, malicious script is injected and permanently stored in a page body, this way user is attacked without performing any actions. The malicious script can access all cookies, session tokens and other critical information stored by the browser and used for interaction with a site. The attacker can gain access to user’s session and learn business-critical information, in some cases it is possible to get control over this information. In addition, XSS can be used for unauthorized modifying of displayed site content. Install this SAP Security Note to prevent the risks. CVSS v3 Base Score: 6.5 / 10
- SAP Business One has an Information Disclosure vulnerability (2588475): An attacker can use Information disclosure vulnerability for revealing additional information (system data, debugging information, etc) which will help to learn about a system and to plan other attacks. Install this SAP Security Note to prevent the risks. CVSS v3 Base Score: 8.4 / 10
- SAP Internet Sales has a Remote Command Execution (RCE) vulnerability (2626762): An attacker can use a Remote Command Execution vulnerability for unauthorized execution of commands remotely. Executed commands will run with a same privileges of a service that executed a command. An attacker can access to arbitrary files and directories located in a SAP-server filesystem including application source code, configuration and critical system files. It allows to obtain critical technical and business-related information stored in a vulnerable SAP-system. Install this SAP Security Note to prevent the risks. CVSS v3 Base Score: 7.5 / 10
- SAP Internet Sales has a Denial of service (DoS) vulnerability (2629
- 535): An attacker can use Denial of service vulnerability for terminating a process of vulnerable component. For this time nobody can use this service, this fact negatively influences on a business processes, system downtime and business reputation as result. Install this SAP Security Note to prevent the risks. CVSS v3 Base Score: 7.3 / 10
- Update to Security Note released on November 2016 Patch Day: OS Command Injection vulnerability in Report for Terminology Export (2357141): Update to a note affecting SAP BASIS, Versions – 7.31, 7.40, 7.50, 7.51, 7.65, 7.66. CVSS v3 Base Score: 9.1 / 10
Enlaces de referencia del CERT del INCIBE en relación a la publicación de las notas para los 3 meses de este trimestre:
- https://www.certsi.es/alerta-temprana/avisos-seguridad/actualizacion-seguridad-sap-abril-2018
- https://www.certsi.es/alerta-temprana/avisos-seguridad/actualizacion-seguridad-sap-mayo-2018
- https://www.certsi.es/alerta-temprana/avisos-seguridad/actualizacion-seguridad-sap-junio-2018
Otras referencias, en inglés de SAP, Onapsis y ERPScan (en orden: Abril->Junio):
- https://blogs.sap.com/2018/04/10/sap-security-patch-day-april-2018/
- https://www.onapsis.com/blog/sap-security-notes-april-%E2%80%9818-testing-assumptions
- https://erpscan.com/press-center/blog/sap-cyber-threat-intelligence-report-april-2018/
- https://blogs.sap.com/2018/05/08/sap-security-patch-day-may-2018/
- https://www.onapsis.com/blog/SAP-Security-Notes-May-18-Hidden-Plain-Sight
- https://erpscan.com/press-center/blog/sap-cyber-threat-intelligence-report-may-2018/
- https://wiki.scn.sap.com/wiki/pages/viewpage.action?pageId=495289255
- https://www.onapsis.com/blog/SAP-Security-Notes-June-18-critical-rereleased-notes
- https://erpscan.com/press-center/blog/sap-cyber-threat-intelligence-report-june-2018/