Inprosec through its services, such as the SAP Security Assessment, helps its customers to improve the security levels of their SAP systems.
March 2021 notes
Summary and highlights of the month
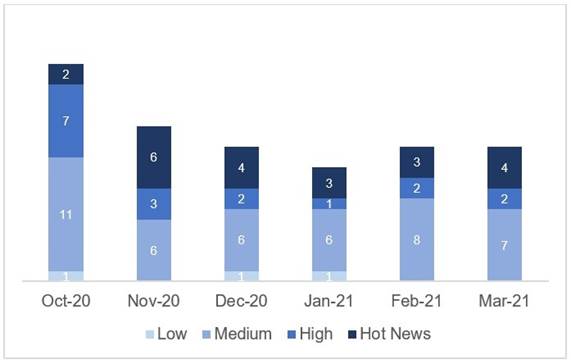
The total number of notes/patches has decreased from last month. Despite this drop in the number of total notes, the number of Hot News increases, being 3 the ones we found last month with respect to the 4 existing in March. On the other hand, it should be noted that the number of notes of high criticality decreased from 2 to 1 this month. As usual we will leave the average and low grades unchecked this month, but will give details of a total of 5 grades (all grades with a CVSS of 7 or higher).
We have a total of 18 notes for the whole month, 2 less than last February (13 from Patch Tuesday, 9 new ones and 4 updates, being the same number of notes as last month).
We have 2 new Hot News, being the total of 4 in this month that stand out for their high CVVS, one of them the recurring update for the SAP Business Client with Chromium . We will also review in detail the only high score of this month (with a CVSS greater than 7) which is also a new score.
- The most critical notes of the month (with CVSS 10) are two updates. One Missing Authentication Check that affects SAP Solution Manager and the other the usual “Browser Control Google Chromium Delivered with SAP Business Client”.
- The next in criticality (with CVSS 9. 9 and 9. 6) is a Code Injection Vulnerability affecting SAP MII and the other one is a Missing Authorization Check affecting SAP NetWeaver AS JAVA (MigrationService).
- From there, we located a single high priority score with a CVSS of 7. 7 being a new score of possible authentication bypass affecting SAP HANA LDAP scenarios.
- This month the most predominant types are “Missing Authorization Check” (5/18 and 4/13 on patch day) and “Reverse Tabnabbing” (4/20 and 1/13 on patch day).
In the graph (post March 2021 from SAP) we can see the ranking of the March notes in addition to the evolution and ranking of the last 5 previous months (only the notes of Sec. Tuesday / Patch Day – by SAP):
Full details
The full details of the most relevant notes are as follows:
- Update – Missing Authentication Check in SAP Solution Manager (User-Experience Monitoring) (2890213): It contains a minor textual update to the possible symptoms of the vulnerability. The note was originally released in March 2020. The last important update of this note was published in November 2020 providing support for an additional support package level of the affected application. CVSS v3 Base Score: 10 / 10 (CVE-2020-6207).
- Update – Security updates for the browser control Google Chromium delivered with SAP Business Client (2622660): This note now includes Chromium version 88.0.4324.150. Compared to the last supported Chromium version (87.0.4280.66), this new version fixes 67 security issues in total, two of them rated by Google as critical (CVE-2021-21117 and CVE-2021-21142). The highest CVSS score of all newly fixed vulnerabilities is 9.6.CVSS v3 Base Score: 10 / 10.
- Code Injection Vulnerability in SAP MII (3022622): It patches a very critical code injection vulnerability in SAP Manufacturing Intelligence and Integrations (SAP MII). SAP MII or xMII (its previous name) is an SAP NetWeaver AS Java based platform that enables real-time production monitoring and provides extensive data analysis tools. It functions as a data hub between SAP ERP and operational applications such as manufacturing execution systems (MES). The software collects data from production machinery, delivering real-time insights into its performance and efficiency. An integral part of SAP MII is the Self-Service Composition Environment (SSCE) that can be used to design dashboards by simple drag and drop. The SSCE allows users to save a dashboard as a JSP file. An attacker can intercept a request to the server, inject malicious JSP code in the request and forward it to the server. When such an infected dashboard is opened in production by a user having a minimum of authorizations, the malicious content gets executed, leading to remote code execution in the server. Some possible actions are: Access to the SAP databases and read/modify/erase any record in any table; Use these servers to pivot to other servers; Place malware to later infect end users; Modify network configurations and potentially affect internal networks. CVSS v3 Base Score: 9.9 / 10 (CVE-2021-21480).
- Missing Authorization Check in SAP NetWeaver AS JAVA (Migration Service) (3022422): It patches a missing authorization check in the Migration Service of SAP NetWeaver AS Java. This service is used internally by the migration framework for migrating applications between major releases of the J2EE Engine. The missing authorization check might allow an unauthorized attacker to gain administrative privileges. This could result in complete compromise of the system’s confidentiality, integrity and availability. As applying the patch that is attached to the note requires a system restart, SAP also provides a temporary workaround that can be deployed online. SAP refers to the workaround as “a notable improvement,” but recommends applying the final patch in parallel as soon as possible. While the workaround just blocks the accessibility to the Migration Service, the final patch adds the missing authorization check to it. CVSS v3 Base Score: 9.6 / 10 (CVE-2021-21481).
- Possible authentication bypass in SAP HANA LDAP scenarios (3017378): It fixes the possibility of an authentication bypass in SAP HANA LDAP scenarios. The authentication bypass is possible if the following conditions apply: The LDAP directory server is configured to enable unauthenticated bind; The SAP HANA database is configured to allow access based on LDAP authentication; SAP HANA is configured to automatically create users based on LDAP authentication. Following the assigned CVSS vector, the vulnerability has a high impact on the system’s confidentiality and integrity. CVSS v3 Base Score: 7.7 / 10 (CVE-2021-21484).
Reference links
Reference links of the CERT of the INCIBE in relation to the publication of the notes for March:
https://www.incibe-cert.es/alerta-temprana/avisos-seguridad/actualizacion-seguridad-sap-marzo-2021
Other references, from SAP and Onapsis (March):
https://wiki.scn.sap.com/wiki/pages/viewpage.action?pageId=571343107
https://onapsis.com/blog/sap-security-notes-march-2021
Resources affected
- SAP 3D Visual Enterprise Viewer, versión 9;
- SAP Business Client, versión 6.5;
- SAP BusinessObjects Business Intelligence Platform (Web Services), versiones 410, 420 y 430;
- SAP Enterprise Financial Services (Bank Customer Accounts), versiones 101, 102, 103, 104, 105, 600, 603, 604, 605, 606, 616, 617, 618 y 800;
- SAP ERP, versiones 600, 602, 603, 604, 605, 606, 616, 617 y 618;
- SAP HANA, versión 2.0;
- SAP Manufacturing Integration e Intelligence, versiones 15.1, 15.2, 15.3 y 15.4;
- SAP NetWeaver:
- Application Server Java (Applications based on Web Dynpro Java), versiones 7.00, 7.10, 7.11, 7.20, 7.30, 731, 7.40 y 7.50;
- AS JAVA (MigrationService), versiones 7.10, 7.11, 7.30, 7.31, 7.40 y 7.50;
- Knowledge Management, versiones 7.01, 7.02, 7.30,7.31, 7.40 y 7.50;
- SAP Payment Engine, versión 500;
- SAP S/4 HANA, versiones 100, 101, 102, 103 y 104;
- SAP Solution Manager (User Experience Monitoring), versión 7.2;