Inprosec through its services, such as the SAP Security Assessment, helps its customers to improve the security levels of their SAP systems.
July 2021 notes
Summary and highlights of the month
The total number of notes/patches has decreased compared to last month. Despite this decrease in the total number of notes, the number of Hot News has remained the same, with 2 notes last month compared to 2 in July. On the other hand, it is worth noting that the number of high criticality notes has decreased from 4 to 2 this month. As usual, we will leave the medium and low scores unchecked this month, but we will give details of a total of 4 scores (all those with a CVSS of 7 or higher).
We have a total of 16 notes for the whole month, 4 less than last June (15 from Patch Tuesday, 12 new and 3 updates, being 4 less than last month).
This month there are 2 critical notes (Hot News), two updates in this case, which stand out for their high CVVS. We will also review in detail 2 of the total of 2 high notes (those of CVSS greater than or equal to 7) where this month would be all new notes.
- The most critical score of the month (with CVSS 10) is an update of the usual “Browser Control Google Chromium Delivered with SAP Business Client” score.
- Next in criticality (CVSS 9), would be an update to last month’s note related to an improper authentication vulnerability, as an ABAP server could not 100% correctly identify whether communication via RFC or HTTP is between application servers in the same SAP system or with servers outside the system.
- From there, we located the 2 notes of high criticality (high priority) being the most relevant with a CVSS of 7.6 a new note of Missing Authorization Check that affects SAP NetWeaver. The rest (12), would be notes of medium and low level, and we will not see them in detail.
- This month the most predominant types are “Information Disclosure” (3/16 and 3*/15 in patch day) and “Missing Authorization Check” (3/16 and 2*/15 in patch day).
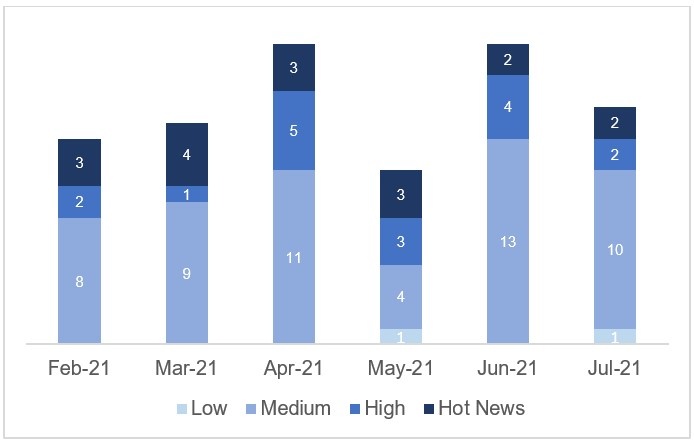
In the graph (post July 2021 from SAP) we can see the classification of the July notes in addition to the evolution and classification of the last 5 previous months (only the notes of Sec. Tuesday / Patch Day – by SAP):
Full details
The full details of the most relevant notes are as follows:
- Update – Security updates for the browser control Google Chromium delivered with SAP Business Client (2622660): This security note addresses multiple vulnerabilities in the 3rd party web browser control Chromium, which can be used within SAP Business Client. This note will be modified periodically based on web browser updates by the open source project Chromium. Security corrections for this browser control are shipped with SAP Business Client patches. If the SAP Business Client release is not updated to the latest patch level, displaying web pages in SAP Business Client via this open source browser control might lead to different vulnerabilities like memory corruption, Information Disclosure and others. CVSS v3 Base Score: 10 / 10
- Update – Improper Authentication in SAP NetWeaver ABAP Server and ABAP Platform (3007182): The vulnerability affects SAP NetWeaver ABAP Server and ABAP Platform, that do not create information about internal and external RFC user in distinguished and consistent format, which may be exploited by malicious users to obtain illegitimate access to the system. The risk of an attack can be reduced by restricting access from network external sources for RFC and HTTP communication in network protection solution accordingly and with the correction provided in this SAP Note the identification of application servers within one SAP system is improved and allows communication to distinguish from application servers of another SAP system or external client and server programs. For the correction, a new Kernel version for RFC and HTTP is required and an ABAP correction for HTTP communication. CVSS v3 Base Score: 9 / 10 (CVE-2021-27610).
- Missing Authorization check in SAP NetWeaver Guided Procedures (3059446): This security note addresses and issue based on that SAP NetWeaver Guided Procedures (Administration Workset) does not perform necessary authorization checks for an authenticated user, resulting in escalation of privileges. The impact is that missing authorization could result to abuse of functionality restricted to a particular user group, and could allow unauthorized users to read, modify or delete restricted data. The affected functions have now been changed and enforced to properly check access restrictions. To correct this problem, implement the Support Packages and Patches referenced by this SAP Note. CVSS v3 Base Score: 7.6 / 10 (CVE-2021-33671).
- Denial of Service (DoS) in SAP NetWeaver AS for Java (Http Service) (3056652): SAP NetWeaver AS Java Http Service stores monitoring data for every HTTP request without properly validating the HTTP method. As result attacker can manipulate the HTTP method and lead to exhaustion of system resources and have direct impact on availability. To solve the issue, update Application Server Java to an SP or release where the issue is fixed and the affected system component provide proper validation of the HTTP request before storing monitoring data. CVSS v3 Base Score: 7.5 / 10 (CVE-2021-33670).
Reference links
Reference links of the CERT of the INCIBE in relation to the publication of the notes for July:
https://www.incibe-cert.es/alerta-temprana/avisos-seguridad/actualizacion-seguridad-sap-julio-2021
Other references, from SAP and Onapsis (July):
https://wiki.scn.sap.com/wiki/pages/viewpage.action?pageId=580617506
Resources affected
- SAP 3D Visual Enterprise Viewer, versión 9;
- SAP Business Client, versión 6.5;
- SAP Business Objects Web Intelligence (BI Launchpad), versiones 420 y 430;
- SAP CRM, versiones 700, 701, 702, 712, 713 y 714;
- SAP Lumira Server, versión 2.4;
- SAP NetWeaver AS ABAP (Reconciliation Framework), versiones 700, 701, 702, 710, 711, 730, 731, 740, 750, 751, 752, 75A, 75B, 75B, 75C, 75D, 75E y 75F;
- SAP NetWeaver AS ABAP y ABAP Platform:
- Versiones 700, 701, 702, 730, 731, 740, 750, 751, 752, 753, 754, 755, 784, 804 y DEV;
- KRNL32NUC, versiones 7.21, 7.21EXT, 7.22 y 7.22EXT;
- KRNL32UC, versiones 7.21, 7.21EXT, 7.22 y 7.22EXT;
- KRNL64NUC, versiones 7.21, 7.21EXT, 7.22, 7.22EXT y 7.49;
- KRNL64UC, versiones 8.04, 7.21, 7.21EXT, 7.22, 7.22EXT, 7.49 y 7.53;
- KERNEL, versiones 8.04, 7.21, 7.21EXT, 7.22, 7.22EXT, 7.49, 7.53, 7.77, 7.81 y 7.84.
- SAP NetWeaver AS for Java:
- Http Service, versiones 7.10, 7.11, 7.20, 7.30, 7.31, 7.40 y 7.50;
- Administrator applications, versión 7.50;
- Enterprise Portal, versiones 7.10, 7.20, 7.30, 7.31, 7.40 y 7.50;
- SAP NetWeaver Guided Procedures (Administration Workset), versiones 7.10, 7.20, 7.30, 7.31, 7.40 y 7.50;
- SAP Process Integration (Enterprise Service Repository JAVA Mappings), versiones 7.10, 7.20, 7.30, 7.31, 7.40 y 7.50;
- SAP Web Dispatcher y Internet Communication Manager:
- KRNL32NUC, versiones 7.21, 7.21EXT, 7.22 y 7.22EXT;
- KRNL32UC, versiones 7.21, 7.21EXT, 7.22 y 7.22EXT;
- KRNL64NUC, versiones 7.21, 7.21EXT, 7.22, 7.22EXT y 7.49;
- KRNL64UC, versiones 7.21, 7.21EXT, 7.22, 7.22EXT, 7.49, 7.53 y 7.73;
- WEBDISP, versiones 7.53, 7.73, 7.77, 7.81, 7.82 y 7.83;
- KERNEL, versiones 7.21, 7.22, 7.49, 7.53, 7.73, 7.77, 7.81, 7.82 y 7.83;