Inprosec through its services, such as the SAP Security Assessment, helps its customers to improve the security levels of their SAP systems.
January 2023 notes
Summary and highlights of the month
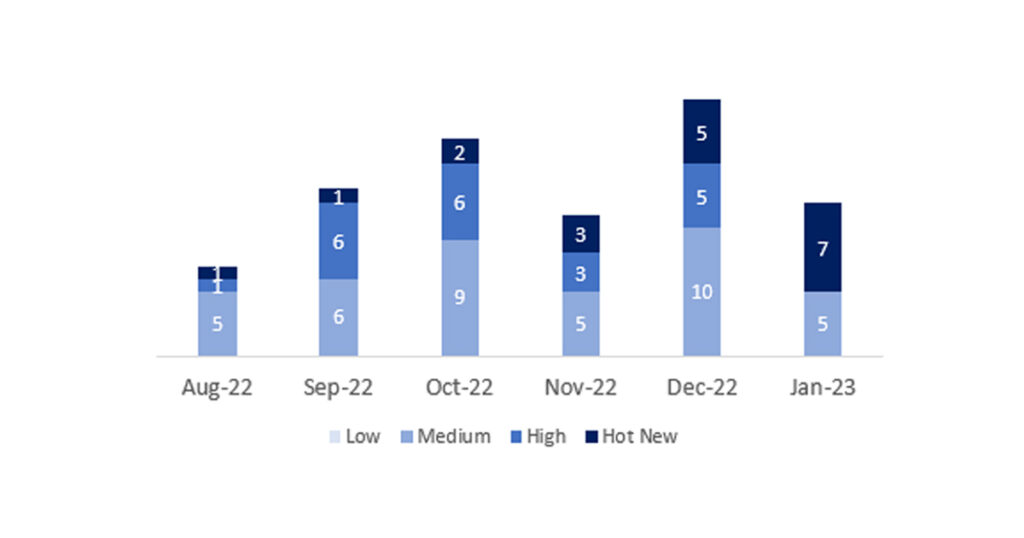
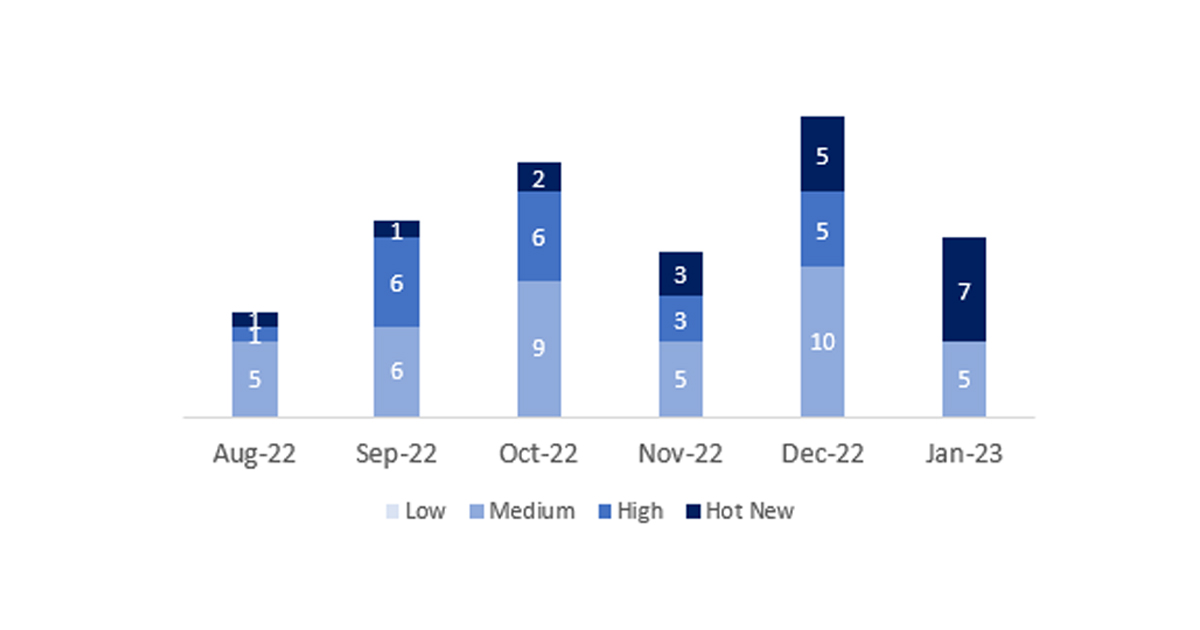
The total number of notes/patches was 12, 8 less than last month. The number of Hot News increased from 5 to 7 this month. On the other hand, it is worth noting that the number of high criticality notes decreases, as there are none this month. As usual we will leave the medium and low notes unchecked this month, but we will give details of a total of 7 notes (all those with a CVSS of 7 or higher).
We have a total of 12 notes for the whole month (the 12 from Patch Tuesday, 9 new and 3 updates, that’s 7 notes less than last month).
We will review in detail the 7 HotNews, 4 of the 7 HotNews are new:
- The most critical notes of the month (with CVSS 9.9) are 4 HotNews, 2 new, one related to Business Planning and Consolidation, “SQL Injection vulnerability in SAP Business Planning and Consolidation MS” and the other one related to Business Intelligence Platform, “Code Injection vulnerability in SAP BusinessObjects Business Intelligence platform”, the following 2 notes, are updates, one related to “Improper access control in SAP NetWeaver Process Integration”, update of a note published in the Patch Day of December 2022, the other updated note is related to Business Intelligence Platform “Insecure Deserialization of Untrusted Data in SAP BusinessObjects Business Intelligence Platform (Central Management Console and BI Launchpad)”, update of a note published in the Patch Day of November 2022.
- The next in criticality (with CVSS 9.4) are 2 HotNews, one related to “Improper access control in SAP NetWeaver AS for Java” and the other related to “Improper access control in SAP NetWeaver Process Integration” (Messaging System), this last note is an update of a note released in the Patch Day December 2022.
- The next criticality note (with CVSS 9.0) is related to “Capture-replay vulnerability in SAP NetWeaver AS for ABAP and ABAP Platform“.
- This month the most predominant type is “Cross-Site Scripting (XSS)” ( 3/12 in patch day).
In the graph (post January 2023 from SAP) we can see the ranking of the January notes in addition to the evolution and ranking of the last 5 previous months (only the notes of Sec. Tuesday / Patch Day – by SAP):
Full details
The complete detail of the most relevant notes is as follows:
- SQL Injection vulnerability in SAP Business Planning and Consolidation MS (3275391) AP Business Planning and Consolidation MS allows an unauthorized attacker to execute crafted database queries. An exploitation of this issue could allow an attacker to access, modify, and/or delete data from the backend database.. CVSS v3 Base Score: 9,9 / 10 [CVE-2023-0016].
- Code Injection vulnerability in SAP BusinessObjects Business Intelligence platform (3262810): SAP BusinessObjects Business Intelligence Analysis edition for OLAP allows an authenticated attacker to inject malicious code that can be executed by the application over the network. On successful exploitation, attacker can perform operations that may completely compromise the application causing high impact on confidentiality, integrity and availability of the application. . CVSS v3 Base Score: 9,9 / 10 [CVE-2023-0022].
- Update – Improper access control in SAP NetWeaver Process Integration (User Defined Search) (3273480): An unauthenticated attacker over the network can attach to an open interface exposed through JNDI by the User Defined Search (UDS) of SAP NetWeaver Process Integration (PI) and make use of an open naming and directory api to access services which can be used to perform unauthorized operations affecting users and data across the entire system. This allows the attacker to have full read access for user data, to make limited modifications to user data and to degrade performance of the system, leading to high impact on confidentiality and limited impact on availability and integrity of the application. CVSS v3 Base Score: 9,9 / 10 [CVE-2022-41272].
- Update – Insecure Deserialization of Untrusted Data in SAP BusinessObjects Business Intelligence Platform (Central Management Console and BI Launchpad) (3243924): There is no verification in the de-serialization process, in some workflow of SAP BusinessObjects BI Platform (Central Management Console and BI LaunchPad), an authenticated attacker with low privileges can intercept a serialized object in the parameters and substitute with malicious serialized one, which leads to deserialization of untrusted data vulnerability. Note update includes a workaround. CVSS v3 Base Score: 9,9 / 10 [CVE-2022-41203].
- Update – Improper access control in SAP NetWeaver Process Integration (Messaging System) (3267780): An unauthenticated user can attach to an open interface exposed through JNDI by the Messaging System of SAP NetWeaver Process Integration (PI). This user can make use of an open naming and directory api to access services which could perform unauthorized operations. The vulnerability affects local users and data, leading to considerable impact on confidentiality as well availability and also limited impact on integrity of the application. These operations can be used to read any information ,modify sensitive information ,Denial of Service attacks (DoS) and SQL injection. This note has been reissued with the correction of SP017 and SP018 of version 7.50. CVSS v3 Base Score: 9,4 / 10 [CVE-2022-41271].
- Improper access control in SAP NetWeaver AS for Java (3268093): An unauthenticated attacker can attach to an open interface and make use of an open naming and directory API to access services which can be used to perform unauthorized operations affecting users and data on the current system. This could allow the attacker to have full read access for user data, to make modifications to user data and to make particular services within the system unavailable. CVSS v3 Base Score: 9,4 / 10 [CVE-2023-0017].
- Capture-replay vulnerability in SAP NetWeaver AS for ABAP and ABAP Platform (3089413): The system identification hash is not unique, SAP NetWeaver ABAP Server and ABAP Platform creates information about system identity in an ambiguous format. This may be exploited by malicious users to obtain illegitimate access to the system, with this note the system ID will become unique. CVSS v3 Base Score: 9,0 / 10 [CVE-2023-0014].
Reference links
Other references, from SAP and Onapsis (January):
SAP Patch Day: January 2023 – Onapsis
Resources affected
- SAP BPC MS 10.0, Versions -800, 810
- SAP BusinessObjects Business Intelligence platform (Analysis edition for OLAP), Versions -420, 430
- SAP BusinessObjects Business Intelligence Platform (Central Management Console and BI Launchpad), Versions -4.2, 4.3
- SAP NetWeaver ABAP Server and ABAP Platform, Versions-SAP_BASIS 700, 701, 702,710, 711, 730, 731, 740, 750, 751, 752, 753, 754, 755, 756, 757, KERNEL 7.22, 7.53, 7.77, 7.81, 7.85, 7.89, KRNL64UC 7.22, 7.22EXT, 7.53, KRNL64NUC 7.22, 7.22EXT
- SAP NetWeaver AS for Java, Version –7.50
- SAP NetWeaver Process Integration, Version –7.50