Inprosec through its services, such as the SAP Security Assessment, helps its customers to improve the security levels of their SAP systems.
January 2022 notes
Summary and highlights of the month
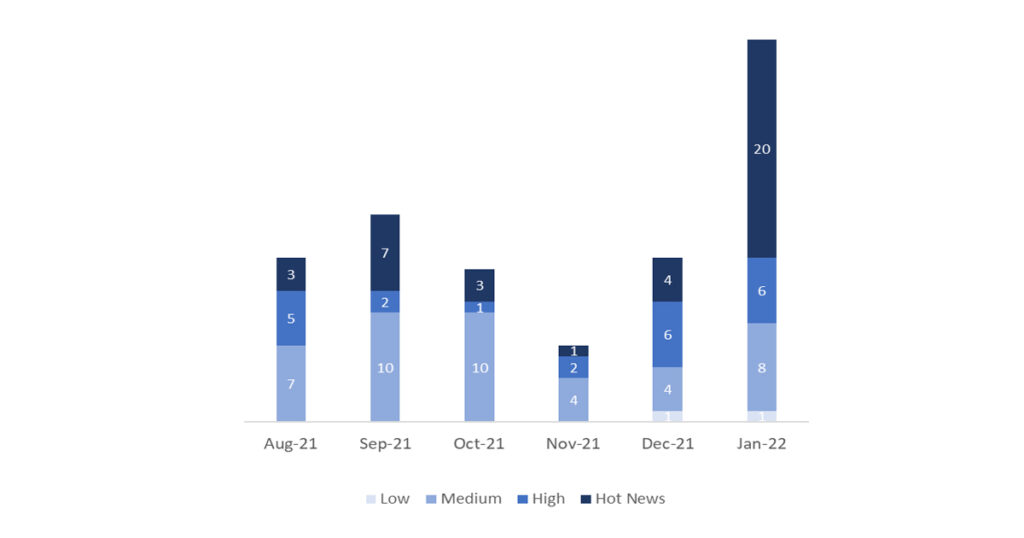
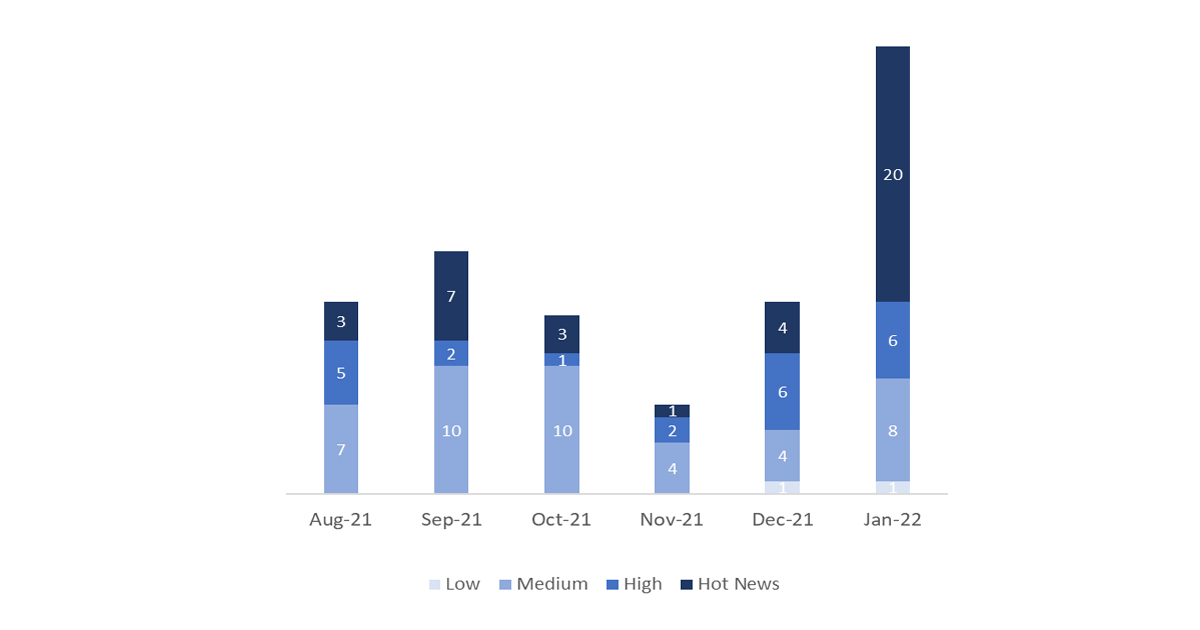
The total number of notes/patches has increased compared to last month. The appearance of the remote code execution vulnerability associated with Log4j has increased the number of notes published by SAP, where the number of Hot News has increased, being 4 the ones we found last month with respect to the 20 existing in January, all linked to the problem with Log4j. On the other hand, it is worth mentioning that the number of high criticality notes remains at 6, 4 of which are also related to Log4j. Due to the variety of components that are being affected by this problem, what SAP has done has been to include all the related notes (both the 20 Hot News, 4 high notes and the rest of the notes) within the central security note 3131047 with a CVSS of 10. Taking this into account, we will leave as usual the medium and low notes without reviewing in this month, but we will give detail of a total of 3 notes (all those with a CVSS of 7 or higher).
We have a total of 35 notes for the whole month, 20 more than last December.
We have 20 new Hot News this month, which stand out for their high relevance and high CVVS. All of these are found within the central security note discussed above. In addition, removing the 4 Log4j high notes that are also located in the central note, we will review in detail 2 of the total of 2 high notes (those of CVSS greater than or equal to 7) where this month we located 1 new and 1 update.
- The most critical note of the month (with CVSS 10) and that is affecting several components is the Central Security Note for Remote Code Execution vulnerability associated with Apache Log4j 2 component. This note, as already mentioned, includes 27 notes of different criticality that affect Log4j.
- The following in criticality (CVSS 8.7 and CVSS 8.4) are two high notes. On the one hand the new note Multiple vulnerabilities in F0743 Create Single Payment application of SAP S/4HANA and on the other hand the update Code Injection vulnerability in utility class for SAP NetWeaver AS ABAP.
- The rest (6) are medium and low level, and we will not see them in detail.
In the graph we can see the classification of the January notes as well as the evolution and classification of the last 5 previous months (only the releases of Sec. Tuesday / Patch Day – by SAP).
Full details
The full details of the most relevant notes are as follows:
1. Central Security Note for Remote Code Execution vulnerability associated with Apache Log4j 2 component (3131047): This security note will be the central document to consolidate information on the Remote Code Execution vulnerability associated with Apache Log4j 2 component (CVE-2021-44228). Apache Log4j2 2.0-beta9 through 2.12.1 and 2.13.0 through 2.15.0 JNDI features used in configuration, log messages, and parameters do not protect against attacker controlled LDAP and other JNDI related endpoints. An attacker who can control log messages or log message parameters can execute arbitrary code loaded from LDAP servers when message lookup substitution is enabled. From log4j 2.15.0, this behavior has been disabled by default. From version 2.16.0, this functionality has been completely removed. Note that this vulnerability is specific to log4j-core and does not affect log4net, log4cxx, or other Apache Logging Services projects. Important: Please refer to the solution section for the list of notes with workaround released by SAP addressing this vulnerability. This security note will be a living document that will be updated regularly. CVSS v3 Base Score: 10 / 10 (CVE-2021-44228).
This note includes the following main «SAP Security Notes»:
| Note |
Component |
Description |
| 3133772 | IS-SE-CCO | Remote Code Execution vulnerability associated with Apache Log4j 2 component used in SAP Customer Checkout |
| 3130578 | BC-CP-CF-RT | Remote Code Execution vulnerability associated with Apache Log4j 2 component used in SAP BTP Cloud Foundry |
| 3132198 | BC-VCM-LVM | Code Injection vulnerability in SAP Landscape Management |
| 3131824 | IS-PMED-HPH | Log4j Vulnerability in Connected Health Platform 2.0 – Fhirserver |
| 3131258 | BC-XS-RT | Remote Code Execution vulnerability associated with Apache Log4j 2 component used in SAP HANA XSA |
| 3132922 | BC-NEO-SVC-IOT | Remote Code Execution vulnerability associated with Apache Log4j 2 component used in Internet of Things Edge Platform |
| 3132744 | BC-CP-XF-KYMA | Remote Code Execution vulnerability associated with Apache Log4j 2 component used in SAP BTP Kyma |
| 3132964 | KM-WPB-MGR | Remote Code Execution vulnerability associated with Apache Log4j 2 component used in SAP Enable Now Manager |
| 3132074 | LOD-CRM-GW-LN | Code Injection vulnerability in Cloud for Customer Lotus Notes PlugIn |
| 3132177 | CA-GTF-CSC-EDO-IN-DC | Remote Code Execution vulnerability associated with Apache Log4j 2 component used in SAP Localization Hub, digital compliance service for India |
| 3132909 | IOT-EDG-OP | Remote Code Execution vulnerability associated with Apache Log4j 2 component used in SAP Edge Services On Premise Edition |
| 3132162 | OPU-API-OD-DT | Remote Code Execution vulnerability associated with Apache Log4j 2 component used in SAP BTP API Management (Tenant Cloning Tool) |
| 3134531 | BC-XS-ADM | Remote Code Execution vulnerability associated with Apache Log4j 2 component used in XSA Cockpit |
| (includes fix provided in 3132822, 3131397) | ||
| 3132515 | IOT-EDG-OD | Remote Code Execution vulnerability associated with Apache Log4j 2 component used in SAP Edge Services Cloud Edition |
| 3131691 | XX-PART-ADB-IFM | Remote Code Execution vulnerability associated with Apache Log4j 2 component used in SAP NetWeaver ABAP Server and ABAP Platform (Adobe LiveCycle Designer 11.0) |
| 3134139 | XX-PART-TRI-CLD-ECT | Remote Code Execution vulnerability associated with Apache Log4j2 component used in SAP Enterprise Continuous Testing by Tricentis |
| 3132058 | IOT-BSV-HS-MS | Remote Code Execution vulnerability associated with Apache Log4j 2 component used in SAP Cloud-to-Cloud Interoperability |
| 3136988 | IOT-BSV-HS-MS | Remote Code Execution vulnerability associated with Apache Log4j 2 component used in Reference Template for enabling ingestion and persistence of time series data in Azure |
| 3136094 | MFG-DM-EDGE | Remote Code Execution vulnerability associated with Apache Log4j 2 component used in SAP Digital Manufacturing Cloud for Edge Computing |
| 3131740 | SBO-CRO-SEC | Remote Code Execution vulnerability associated with Apache Log4j 2 component used in SAP Business One |
| 3135581 | BC-XI-CON-JWS | Remote Code Execution vulnerability associated with Apache Log4j 2 component used in Java Web Service Adapter of SAP NetWeaver Process Integration |
| (includes fix provided in 3132204, 3130521, 3133005) |
2. Multiple vulnerabilities in F0743 Create Single Payment application of SAP S/4HANA (3112928): It patches a Cross-Site Scripting and a Code Injection vulnerability in the Create Single Payment app of S/4HANA (app ID F0743). This app is used by accounts payable accountants through SAP Fiori (SAPUI5). It allows them to make a direct payment to a supplier when no invoice exists as well as pay open supplier line items. The two vulnerabilities existed because uploaded and downloaded files were not checked by the app. The first vulnerability allows an attacker with basic user rights to run arbitrary script code, resulting in sensitive information being disclosed or modified. The second one enables an attacker with basic user rights to inject dangerous content or malicious code which could result in critical information being modified or completely compromise the availability of the application. CVSS v3 Base Score: 9.8 / 10 (CVE-2022-22531).
3. Update – Code Injection vulnerability in utility class for SAP NetWeaver AS AB (3123196): This note has been updated with some information about its validity. The original validity interval is only valid for SAP customers using the license-bound product Post-Copy Automation (PCA). For all other customers, the minimum patch level of the validity interval has been increased. CVSS v3 Base Score: 8.3 / 10 (CVE-2021-44235).
Reference links
Reference links of the CERT of the INCIBE in relation to the publication of the notes for January:
https://www.incibe-cert.es/alerta-temprana/avisos-seguridad/actualizacion-seguridad-sap-enero-2022
Other references, from SAP and Onapsis (January):
https://wiki.scn.sap.com/wiki/pages/viewpage.action?pageId=596902035
Resources affected
- Internet of Things Edge Platform;
- Reference Template for enabling ingestion y persistence of time series data in Azure;
- SAP BTP:
- API Management (Tenant Cloning Tool);
- Cloud Foundry;
- Kyma;
- SAP Business One, versión – 10;
- SAP Business One;
- SAP Cloud for Customer (add-in para Lotus notes client);
- SAP Cloud-to-Cloud Interoperability;
- SAP Connected Health Platform 2.0 – Fhirserver;
- SAP Customer Checkout;
- SAP Digital Manufacturing Cloud para Edge Computing;
- SAP Edge Services Cloud Edition;
- SAP Edge Services en Premise Edition;
- SAP Enable Now Manager;
- SAP Enterprise Continuous Testing by Tricentis
- SAP Enterprise Threat Detection, versión – 2.0;
- SAP GRC Access Control, versiones – V1100_700, V1100_731, V1200_750.
- SAP HANA XS Advanced Cockpit (includes correction provided in 3131397, 3132822);
- SAP HANA XS Advanced;
- SAP Landscape Management;
- SAP Localization Hub, servicio de conformidad digital para la India;
- SAP NetWeaver:
- ABAP Server y ABAP Platform (Adobe LiveCycle Designer 11.0);
- AS for ABAP y ABAP Platform, versiones – 701, 702, 711, 730, 731, 740, 750, 751, 752, 753, 754, 755, 756, 786;
- Process Integration (Java Web Service Adapter) (includes correction provided in 3132204, 3130521, 3133005);
- SAP S/4HANA, versiones – 100, 101, 102, 103, 104, 105, 106;