During this article we are going to focus on the integral service SAP Security Assessment (SSA), which gives the opportunity to have truthful information in real time about the main risks and unsecure configuration settings that can compromise the security of the system (confidentiality, integrity and availability of the information) in SAP systems.
To begin with, it will be detailed what security checks has this service, what can we expect from it and finally an example of one of the technical controls will be shown.
Security Checks
This SAP Security Assessment has more than 40 security checks distributed in 3 big groups:
- Installation
- Security
- System Status
INSTALLATION
In this section, all software versions are checked in the different SAP components. Furthermore, all implemented security notes in the system are also checked and validated.
SECURITY
This is the main category of the security assessment, and which has the following sections:
- Users and their passwords.
- Authorization checks.
- RFC connections and web services.
- Configurations related to the client.
- SNC & SSO (Security Network Connection & Single-Sign On)
- Audit logs and security files.
- Custom code (Z).
SYSTEM STATUS
This last category is related to the system performance and the maintenance status of the Jobs.
SAP Security Assessment
Once the introduction of this service has been done, now we will describe the structure of how each control is done inside the SSA.
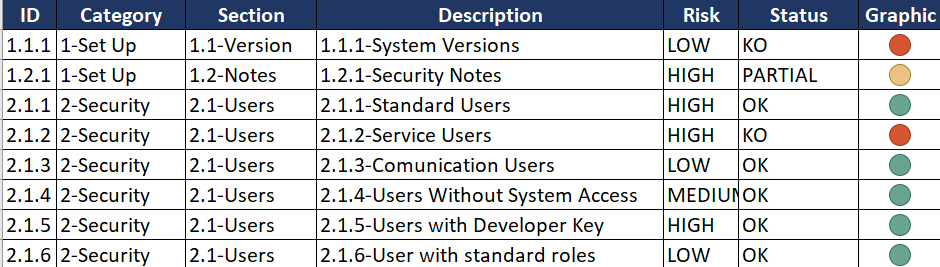
Each control will have its own table with the following structure:
| Risk | It is rated on a scale of Low/Medium/High, depending on the impact that the threat may have on the system, and the probability of this happens. |
| Detail | Short description of the information analysed in the control. |
| Threat | Description of the security incidents that may occur in the system, in case of security deficiencies. |
| Environment | Specifies the environment in which the control will be analysed and in which the information will be extracted. It may be one of the environments or a combination of them: PRD, QAS y DEV. |
| Advice | Group of proposals focused on mitigating or solving a deficiency detected in one of the controls. |
It is relevant to note that, these controls are done in different type of SAP systems such as NetWeaver AS ABAP, NetWeaver AS JAVA and HANA data bases. In addition, for most controls, the only environment to consider will be the productive one (PRD), but there are some exceptions in which it will also be necessary to analyse the settings in quality environments (QAS) and development (DEV). Even in some case, only the development environment will be analysed:
- Controls in which they will be analysed in PRD, QAS and DEV:
- Standard Users.
- Password Cracking.
- Remote Logon.
- Controls in which it will be analysed only in DEV:
- Security Notes.
- Authorization Checks.
- Custom Tcodes code
Finally, in each control will be detailed the compliance status, which according to predefined criteria, it evaluates the state of the system respect to that control and if it is OK, PARTIAL or KO:
Security Control: Password Cracking
So based in the previous point, the case of one of the controls that are part of the SAP Security Assessment will be detailed.
On this occasion, will be commented this analysis about the password encryption method used with SAP users, which may use obsolete algorithms that could be cracked with external brute force tools.
The following table provides all the information related to the control:
| Risk | High (High Impact, High Probability) |
| Detail | Analysis of the hash used to encrypt the passwords and password cracking test. The MD5 hash type (BCODE field) and SHA1 (PASSCODE field) are easily decipherable |
| Threat | The use of old encryption methods (hashes) makes it easier for an attacker to obtain user passwords. To obtain the hash of the passwords, it is enough to obtain the information from one of the following tables: USH02, USH02_ARC_TMP, USR02, USRPWDHISTORY, VUSER001, VUSR02_PWD.
Because password decryption is performed outside the SAP system, there are no options to prevent the brute force attack. |
| Environment | PRD, QAS, DEV |
| Advice | Set the value 0 in the parameter login/password
_downwards_compatibility. Run the CLEANUP_PASSWORD_HASH_VALUES program to remove old hashes. Increase the security of the password policy. Include most used passwords in the list of prohibited words in the USR40 table, to make decryption by brute force harder to the attacker. |
The key for this control is based on the <login/password_downwards_compatibility> parameter, which manages compatibility with legacy versions of encryption types on BCODES. These alphanumeric “BCODE” elements are a hash that corresponds to the first 8 characters of a user password. Because these elements are stored in tables, there is a chance that an attack could reach one of these containers and obtain the values. Whether the parameter allows obsolete encryption methods such as MD5 (128-bit cryptographic reduction algorithm) or the SHA1 (160-bit hash value), decryption using external brute force tools it is highly probable.
Furthermore, another possible recommendation to make it more difficult for attackers is to create a list of prohibited words (table USR40) which no employee will be able to use for his login password. For example, this can have words such as:
- Top 10 most used passwords (Password, Admin, qwerty, 123456….)
- Company name or derivatives
- Names of employees, plants or products
- Birthday days
- Name of the months
Key Points to Take Home
- The SAP Security Assessment offers a snapshot of the current state of the SAP system with real and truthful information.
- It allows to detect deficiencies in the current technical configuration.
- A detailed results report is included together with a letter of recommendations for each control.
- These security checks can be automated in Configuration Validation, one of the Solution Manager tools that we will explain specifically in another article.